
Fivecomm
ID: 3915
February 2, 2022
5G enabled autonomous and remote controlled intelligent mobile robots.
ID: 3944
February 21, 2022
Quadible is a cybersecurity specialist that helps organisations mitigate identity and financial fraud by offering an artificially intelligent platform with the ability to authenticate end-users based on behavioural patterns. The London-based company was founded in 2015, and the team of today comprises eight people in an experiential fusion of software engineers and researchers.
Authentication systems are nowadays becoming an integrated component for commercial websites and internal corporate databases. Often, such systems rely on externally provided platforms in order to enhance overall security and restrict unauthorised access to the website or database. These platforms have three purposes:
Quadible’s platform authenticates users by combining the conventional metrics of authentication with multiple behavioural traits, which enable the platform to determine user patterns, e.g. how a person moves, how he/she uses his/her devices, how he/she make transactions, what the person’s biometrics are, etc.
“We combine more than 14 different behavioural traits to continuously assess if the person that is trying to access a particular service is exactly who they say they are.”
Niklas Palaghias, CEO at Quadible
Behavioural patterns constitute a unique characteristic of people in their daily life, which provides valuable information in the process of identifying and verifying the users of online services. The artificial intelligence (AI) of the platform basically learns behavioural patterns in order to continuously assess the authenticity of users.
Customers of Quadible’s solution include a wide variety of organisations that somehow mediate information online. These are primarily banking and financial service institutions, and secondarily health care facilities. Any organisation that maintains a database containing sensitive or classified information (typically in sectors such as manufacturing, construction, tech, marketing etc.) is a potential user of the platform.

The incentive of Quadible to develop their IoT solution derives from the public ambition to build a secure cyberspace environment. As essential services and critical sectors have become ever more dependent on digital technologies, the increase in physical objects connected to the internet has exploded – and the phenomenon of cyber-attacks has escalated as a direct consequence.
The main target of Quadible is to drive technology to improve people’s lives in a societal manner. The company seeks to do so by delivering a software product that reduces the risk of cyber-attacks and protects against the unauthorised exploitation of systems, networks and technologies.
Quadible was founded as a consultancy. However, soon after learning about the cybersecurity challenges faced by their customers, and due to their engagement in various projects with thought leaders in the field, the company realised that there are still major challenges in certain aspects of cyber authentication that need to be addressed.
The traditionally deployed method, the two-factor authentication [1], which characterises the majority of the solutions available on the market, is compromised and not fully competent to handle the major demand for and requirements to cybersecurity set by the Next Generation Internet. These current systems are inconvenient, cause a bad user experience, have substantial associated costs due to operational inefficiency and rapid fraud, and they represent huge risks due to breaches in security and privacy. The fundamental issue of the two-factor authentication method is that it relies on an ‘identity approximation’ system, which seeks to grant access to individuals based on known devices, but hackers have become adept at subverting this system. In fact, the 2020 index [2] indicated that 39% of EU citizens experience security-related problems. The damage caused by cyber-attacks goes beyond single organisations to civil economy and finance, testing the resilience of democratic states and institutions, and thereby threatening the basic functioning of society.
Quadible decided to combine their experience in cybersecurity with human behaviour recognition software to develop an innovative platform solution to address the challenge.
“We leverage IoT to enhance the data that we collect – the behavioural data – and we use that to authenticate people.”
Niklas Palaghias, CEO at Quadible
Highly motivated to proliferate the quality of authentication systems and to increase the security and privacy of their customer’s services, Quadible started developing their authentication platform in 2017. To ensure remarkable quality and superiority of the solution, it was developed on premises such as data storage and processing within the EU, encryption both at device and infrastructure level and data anonymisation.
The fundamental offering of Quadible is user authentication in terms of a reliable platform for online mediators to verify the identity of end-users before granting them access to their service, thereby preventing risks of fraud and data breaches.
The Quadible platform is actuated when an end-user requests access to the service of the online mediator. As an end-user, you do not need to provide information in terms of credentials to let the authentication system know 1) who you are, and 2) that it is actually you. Through a variety of behavioural and biometric information, the platform is able to determine if you are, who you are saying that you are. In addition to this information, a variety of data is collected through the device used by the end-user. Embedded in the device are sources of data such as accelerometer, gyroscope, magnetic field and network traces, which provide information on the location, navigation and movements of the user. This is complemented by the collection of biometric data such as facial recognition and fingerprint scan, as well as behavioural data in terms of device usage, app usage and transactional data.
All data is mapped to a pseudo ID that anonymises the end-user, and it is then transmitted to the Quadible platform. The platform runs on a cloud infrastructure with connectivity supported by the 4G cellular network, Wi-Fi and Ethernet. The data is processed by the platform, and AI technology is then deployed to either confirm or reject the authenticity by comparing the information provided by the pseudo ID and the information provided by the end-user. If Quadible’s platform verifies that there is compliance between pseudo ID and end-user, the authentication system of the online mediator will grant access to the service. If compliance cannot be verified, it is likely because the end-user is a fraudster, and access to the service will then be denied.
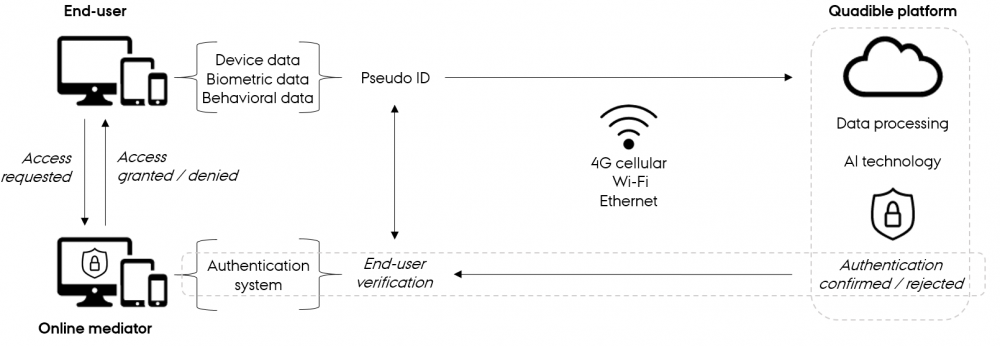
From the perspective of end-users, there is no direct interaction with the Quadible platform because it is running as a back-end system in the service of the online mediator, and hence as an integrated security component. Complementary to the actual end-user authentication, Quadible’s solution provides risk scores to the customers, and they are also in the process of developing dashboards for visualisation of aggregated data insights and analytics.
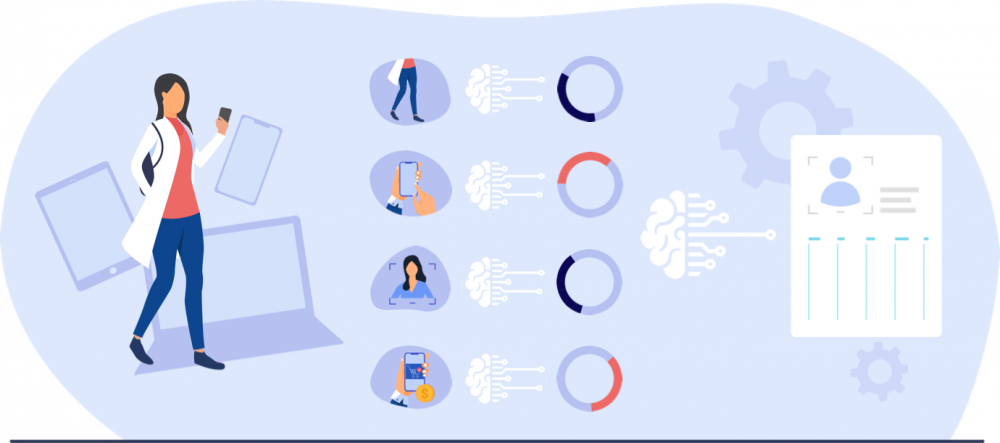
Authentication systems as an offering are not new to the market, but the inclusion of behavioural traits of the users, as well as the use of AI to access the verification, adds a new dimension to traditional authentication. The traits detected include:
The amount and combination of traits deployed by Quadible’s platform allow the system to achieve ultra-high authentication confidence and accuracy on verifying users who are accessing a particular online service at any point in time. The detection of behavioural traits is valuable both in enabling multi-factor authentication [3] and in gaining an understanding of user behaviour. Insights on these traits are a valuable source of inspiration for online mediators to generate enhanced value propositions. The use of AI technology on top empowers the security and privacy of the solution, as it combines the behavioural traits and multiple biometrics, eliminating the errors of each individual method.
“IoT provides us with the ability to authenticate users both through the context but also through the perspective of the user.”
Niklas Palaghias, CEO at Quadible
The development of Quadible’s IoT solution is a direct contribution to the configuration of a more secure and future-proof cyberspace environment. By rethinking the methodologies of authentication, Quadible has designed a more intelligent solution that is not only able to minimise the risk of cyber-attacks but also contributes to improving the end-user experience and increasing the overall security and competitiveness of online services.
“Due to the COVID era and increase of digitalisation, a further increase of fraud is taking place, so we see more and more organisations wanting to adopt such a solution.”
Niklas Palaghias, CEO at Quadible
The beneficial outcomes of having secure authentication systems – or rather, the scare stories of not having one – have become highly noticeable during the recent decade. Concurrently with a heavy increase in the number of online users and services, and a global pandemic that has accelerated the digitalisation trend even more, immense opportunities for cyber-criminals and fraudsters exist, and unfortunately, identity theft, financial fraud and data breaches have increased exponentially. So has the demand for Quadible’s solution.
The increasing demand is manifested as an outcome in terms of the reshaping of Quadible’s original value proposition, transforming the company from being a service provider to being a SaaS provider. This IoT-driven transformation has enabled the company to up-scale the business, generating company growth as an outcome as well. Quadible generates profit from a recurring revenue mechanism where customers are charged per year and per user, creating a continuation in the revenue as well as in the interactions with customers.
“For sure we are next to them, and if they require some type of improvement, some additional features or services, we are there to provide that also.”
Niklas Palaghias, CEO at Quadible
For users of the solution, the direct outcome is a highly secure and user-friendly system that enables online mediators to authenticate end-users – and simultaneously improves the end-user experience and reduces costs by automating the process. The key feature and unique trait of the system are that it uses the method of multi-factor authentication. It essentially results in a frictionless authentication mechanism that, without the need of any user input such as usernames and passwords, increases security and customer satisfaction throughout the process while being an affordable line of business both in terms of the technology and in terms of mitigating risks of fraud and breaches in security and privacy. For customers of the solution, the main beneficial outcomes can be summarised into:
Likewise, for end-users of the system, the multi-factor authentication offers beneficial outcomes that enhance the user experience and thereby increase user acceptance. For example:
The beauty of Quadible’s multi-factor authentication solution is its ability to link access privileges to real people, rather than devices and passwords. The platform does not make assumptions about ownership and knowledge with biometrics but considers also human identity and behaviour. This makes it much more difficult for criminals to impersonate authentic users, thereby making networks, databases and websites more secure.
The solution offered by Quadible is still a novel technology, and in the early days after the foundation of the company, organisations were often reluctant to adopt it. However, as digitalisation and cyberspace – along with its associated security challenges – have accelerated, so has the basic understanding of and openness towards Quadible’s solution. The company points out the advantage of selling IoT-empowered solutions to customers with IoT-empowered business models as it eases adoption and breeds promising prospects.
“We see more and more organisations being interested in adopting this type of risk-based authentication. …Our customers fully understand the unique selling point that we are offering.”
Niklas Palaghias, CEO at Quadible
An essential learning for Quadible has been the power of using IoT to tap into a widely recognised user problem. Letting the customers guide development, while collecting support from advisors in the process, partners and colleagues in the field have, according to Quadible, played a significant role in reaching the current state of achievement.
Quadible considers a number of points to be vital for the success of their IoT platform solution. Taking departure in this solution of intelligent authentication offered concurrently with a rising need for cybersecurity, these points are compiled into a list of recommendations below.
1. Provide value that justifies the customer’s spending
For any IoT innovator striving for success, it is of course essential to find a use case that enables one to provide value to one’s customers. In the process, Quadible emphasises the crucial factor of being able to compellingly justify to one’s customers the money they are spending on one’s solution.
“It is a very important element to be able to show why they should buy the solution and what the benefit is.”
Niklas Palaghias, CEO at Quadible
2. Identify the pain of the users and develop a solution that solves it!
Offering a solution that addresses the end-user pains is the most effective way of tapping into the customer demand of any B2B market scenario. One of the motives behind Quadible’s deployment of the multi-factor-authentication method is a derived demand from end-users being frustrated with the process of creating and submitting usernames and passwords.
“They are looking for more innovative solutions that will discard, for example, the element of passwords. So for sure, we are looking into that!”
Niklas Palaghias, CEO at Quadible
3. Structure the company towards innovation
Quadible ascertains great value in their own learnings concerning structuring the company properly in alignment with an innovative value proposition. This has included meticulous planning around the legal aspects, the technological commercialisation, the organisation and obtaining financial and human resources. Utmost essential for the structure, however, is that it is fostered by the company culture.
“It is very important to keep the team challenged and knowing that they are working on a high-end innovative product.”
Niklas Palaghias, CEO at Quadible
4. Leverage know-how to develop complementary products
“The know-how that we have internally in the company has played a significant role to be able to develop this type of technology.”
Niklas Palaghias, CEO at Quadible
When using distinctive internal knowledge resources in creating the value that is offered to one’s customers, Quadible points out the often unexplored potentials of further leveraging that know-how to develop complementary products that enhance the value offering and build a more holistic solution. In this case, the leverage of knowledge from consulting in human behaviour recognition, user identification and cybersecurity enabled the company to advance the platform solution to target multiple sectors.
Finally, there is just one indispensable recommendation from Quadible that cannot be left unsaid:
“I would say by all means: go for it! It is a very interesting and enjoyable journey.”
Niklas Palaghias, CEO at Quadible
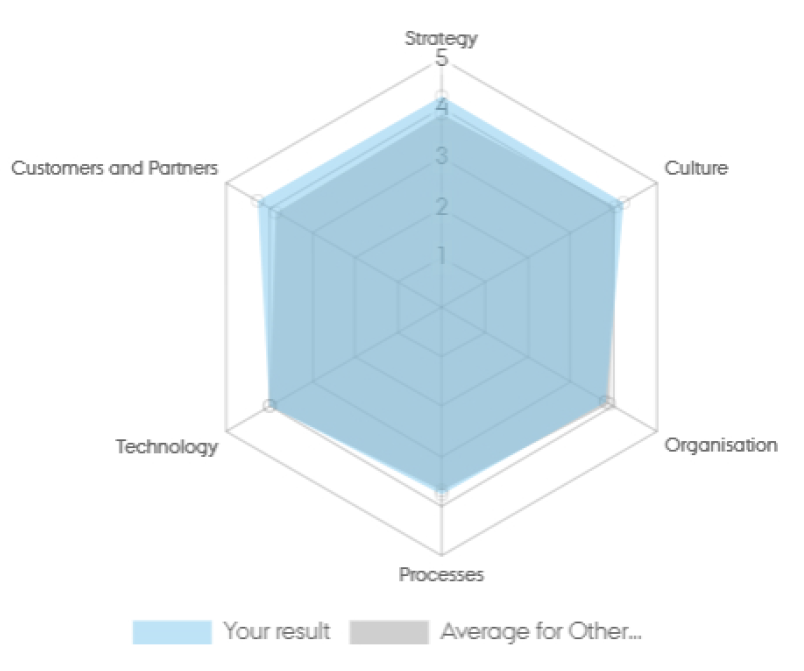
Illustration 5: Digital Maturity Radar Chart: Assessment of Quadible by Niklas Palaghias, CEO and Founder.
Quadible assumes a high level of digital maturity with an overall score of 4.04. The score indicates that the digital capabilities of the company are vastly mature, and that they perform above average for the sector.
The Digital Maturity Assessment Tool is copyrighted by Associate Professor and PhD Annabeth Aagaard, Director at the Interdisciplinary Centre for Digital Business Development, Aarhus University. To get the digital maturity of your company mapped out, click here.
[1] Two-factor authentication: electric authentication system in which a computer user receives access to a particular network, platform or application only after providing two independent sources of identifying evidence – typically a password and a physical token (e.g. a debit card or a passcode or QR code that is generated by a third party security system and sent to the user’s cell phone).
[2] EUReporter: Why cybersecurity in the EU should matter to you
[3] Multi-factor authentication: electric authentication system in which a computer user receives access to a particular network, platform or application only after providing multiple independent sources of identifying evidence.

Copyright notice: © 2020 – 2023 EU-IoT Consortium.
This material was produced as part of the EU-IoT project, grant ID 956671, and is funded by the Horizon 2020 Framework Programme under topic ID ICT-56-2020.
EU-IoT is the European IoT Hub. The EU-IoT project works towards growing a sustainable and comprehensive ecosystem for Next Generation Internet of Things.
Source of origin: Information to document this use case originates from a network collaboration w. IoT Next Club (IoT community associated with the NGIoT initiative); Case period: 2021-2022.
