Introduction
This section serves as a supporting resource for the Toolbox. Here, you will find a complete introduction to the IoT door lock system, along with all the example tools, providing a clear overview of how the examples are interconnected throughout the analysis.
We use an IoT door lock system as a running example in all the example tools, providing a clear overview of how the tasks are interconnected throughout the risk analysis.
This Smart Door Lock is based on an IoT system and is designed to optimize your home's autonomy and security.
The solution is designed for a typical family home, where all family members can access the house using an app on their mobile phones or through a physical device mounted at the entrance. This eliminates the need for physical keys, which children can easily lose or forget, often resulting in expensive locksmith services or even the need to replace all physical locks in the home.
Additionally, this system can be integrated with broader building monitoring and management systems. This allows homeowners to not only control access but also monitor entry and exit activities, track lock status remotely, and receive notifications in case of unusual activity, providing an extra layer of security and convenience.
In the next section you will get a more detailed overview of the system and dataflows.
System overview: The IoT doorlock
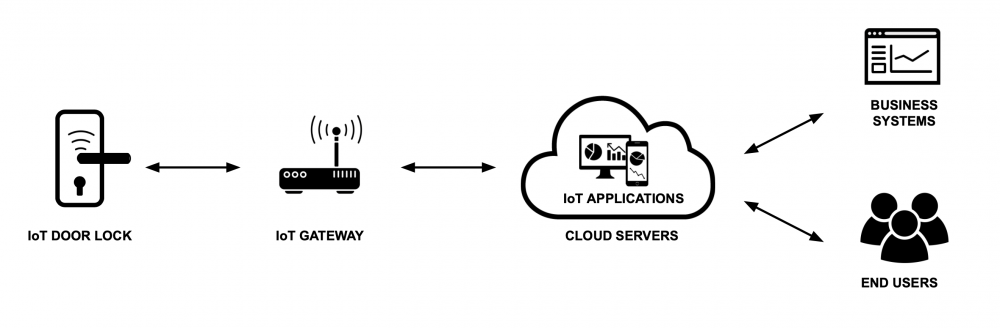
Illustration: Key enabling technologies for the IoT door lock solution.
IoT Door Lock Hardware
Lock Mechanism: This is the physical component that secures the door. It receives commands to lock or unlock, typically from a microcontroller.
Zigbee Module: A wireless module that allows the door lock to communicate with the gateway. It listens for commands to lock or unlock and can send status updates.
Microcontroller: The "brain" of the door lock. It processes commands received via the IoT door lock, controls the lock mechanism, and manages power to ensure efficient battery usage.
Gateway (Hub):
Receiver/Transmitter: Communicates wirelessly with the door lock's wireless communication module.
Wired/Wireless Connectivity to Cloud: This could be through Ethernet, Wi-Fi, cellular, etc. It serves as the bridge between the IoT door lock’s local network and the cloud infrastructure.
Local Processing (Optional): Can process some commands locally, potentially allowing for quicker responses or functioning even if cloud connectivity is interrupted.
Cloud-based System:
Data Storage: Stores historical data, such as lock/unlock events, user access logs, battery levels, and more.
Processing Server: Processes requests from the mobile application, communicates commands to the gateway, and can handle more complex tasks like analyzing usage patterns or sending alerts for suspicious activities.
API Server: Handles API calls from the IoT application, allowing for functions like remote lock/unlock, checking lock status, and configuring user access.

IoT Mobile Application:
User Interface: Allows users to interact with the IoT door lock system. Features might include lock/unlock buttons, viewing access logs, and receiving notifications.
Communication with Cloud: The app communicates with the cloud-based system via API calls to get status, send commands, or configure settings.
Local door lock Control (Optional): In some advanced setups, the mobile device might have direct communication capabilities to the door lock, allowing it to control the lock directly when in proximity.
Data Flow:
- The IoT application sends a command (e.g., lock/unlock) via the cloud system.
- The cloud system processes the command and forwards it to the gateway.
- The gateway, using the wireless module, communicates the command to the IoT door lock.
- The door lock processes the command and acts (locks/unlocks), then sends a status confirmation back up the chain to the user's application.
End notes
- Howard, M., & LeBlanc, D. (2003). Writing Secure Code. Microsoft Press.
- details on the STRIDE methodology.
- European Commission. (2019). Directive on the European Electronic Communications Code (RED). Official Journal of the European Union.
- RED regulatory considerations.
- European Union Agency for Cybersecurity. (2020). NIS Directive: Technical Guidelines for the Implementation of Minimum Security Measures.
- NIS2 regulatory considerations.
- OWASP Foundation. (2023). OWASP Internet of Things (IoT) Top Ten. OWASP.
- This resource provides a list of the top ten most critical web application security risks, which could be used for historical data and known vulnerabilities.
- IoT Security Foundation. (2018). IoT Security Compliance Framework.
- A resource that might be cited for industry best practices.
- Dhanjani, N. (2015). Abusing the Internet of Things: Blackouts, Freakouts, and Stakeouts. O'Reilly Media.
- Data Protection Commission. (2021). Guidelines on Data Privacy in IoT. DPC Publications.
- insights into the data privacy threats and regulatory considerations for IoT systems.

