
Outline
The module in brief
-
EU product legislation
-
Network and Information Security Directive (NIS2)
-
Obligations under NIS2
-
Cyber Resilience Act (CRA)
-
Obligations under the CRA
-
Radio Equipment Directive (RED)
-
Obligations under the RED
-
Additional resources and knowledge
-
Expert advice
-
Output
-
Next step
March 20, 2025
Before you start
This learning module is part of the building block:
The module in brief
This module provides an overview of current IoT cybersecurity legislations for manufacturers and your products. It covers the most relevant legislations, their impact, and how they interact with general product legislation within the EU.
"Directives and regulations" by CyPro available under licensen CC BY-NC-ND
Practical information
The module offers a concise overview that can be learned in just 15 minutes. The content is targeted at product owners, developers, project managers and compliance officers. It is recommended that at least product owners or similar are involved in the process of evaluating the impact of legislation in your organisation and business.
EU product legislation
With regard to product legislation in the EU, the CE mark is generally the first thing that comes to mind. This marking is intended to show the owner or user of a product that the product complies with the essential requirements outlined in various pieces of legislation, each addressing different areas of product safety. Examples include the Toy Safety Directive, the Low Voltage Directive and the Radio Equipment Directive.
Overall, EU product legislation is structured according to what is known as the New Legislative Framework (NLF). This framework aims to harmonise the underlying laws to ensure a consistent format, thereby making it easier to work with requirements imposed by different pieces of legislation. Requirements come in two forms: directives and regulations. The main difference between them is that regulations apply directly to products and are uniform across member states, whereas directives must be implemented through national law in each member state, which may result in minor variations in national implementations.
For cybersecurity, there are three main pieces of legislation:
- The Network and Information Security Directive (NIS2)
- The Cyber Resilience Act (CRA)
- Delegated Regulation 2022/30 under the Radio Equipment Directive
Network and Information Security Directive (NIS2)
The NIS2 Directive concerns the protection of what are known as important and essential entities. These are companies and organisations whose services, activities and products our society relies on to maintain its operations. Being a directive, it must be implemented into national legislation in each member state. Thus, there may be variations in national NIS2 requirements across the member states. Therefore, NIS2 in Denmark and Germany are not necessarily identical.
To be covered by NIS2, there are certain requirements that must be met. Firstly, your company must exceed the medium-sized enterprise thresholds. This means you must employ at least 50 people and have an annual turnover or total balance of more than €10 million. Secondly, your primary activities must fall within one or more of the sectors listed in Table 1 and Table 2 below. Some areas are covered solely by virtue of their activities. For example, providers of public electronic communications networks, domain name systems, and others offering services whose disruption could impact public safety and health. If you are unsure whether you are covered by any of these special rules, it is recommended to read Article 2 of the directive and consult the relevant authority responsible for the area in question.
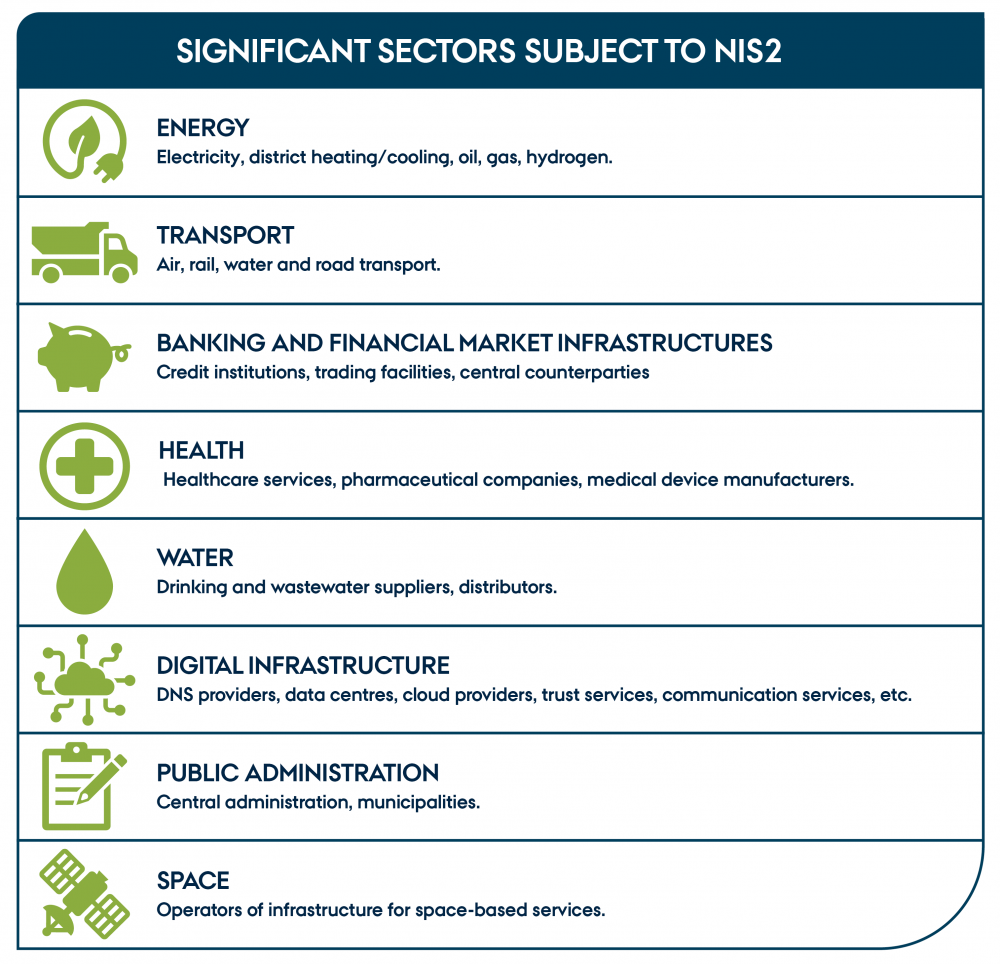
"Significant sectors subject to NIS2" by CyPro under licence CC BY-SA 4.0
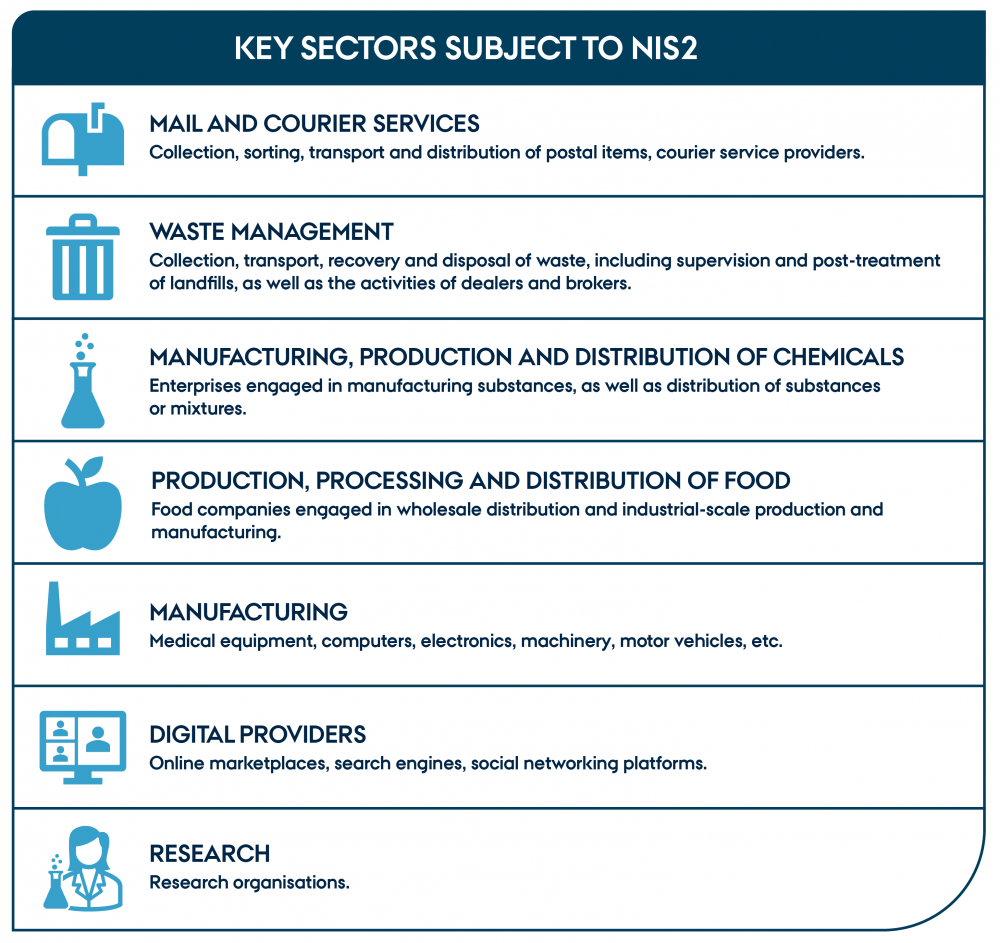
"Key sectors subject to NIS2" by CyPro under licence CC BY-SA 4.0
Obligations under NIS2
If your company is covered by NIS2, there are a number of requirements you must meet. In general, companies subject to NIS2 are under an obligation to implement:
appropriate and proportionate technical, operational and organisational measures.
These measures must be based on all the risks that may exist in relation to the services you provide.
The measures implemented must include at least:
- Risk analysis and information system security policies
- Incident management
- Business continuity, such as backup management and disaster recovery, as well as crisis management
- Supply chain security, including security-related aspects concerning the relationship between each entity and its direct suppliers or service providers
- Security related to the acquisition, development and maintenance of network and information systems, including the management and disclosure of vulnerabilities
- Policies and procedures for assessing the effectiveness of cybersecurity risk management measures
- Basic cyber hygiene practices and cyber security training
- Policies and procedures regarding the use of cryptography and, where applicable, encryption
- Personnel security, access control policies and asset management
- Use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications, and secured in-device emergency communication systems, where applicable.
- In other words, it is about leading the processes that support cyber and information security activities in the entity.
Cyber Resilience Act (CRA)
The Cyber Resilience Act, or simply CRA, is a regulation that introduces mandatory requirements on products with digital elements defined as:
"a software or hardware product and its remote data processing solutions, including software or hardware components that are placed on the market separately"
This essentially means all electrical and electronic products that transmit data in one way or another. The requirements set out in the regulation are part of the essential requirements that come as part of the CE marking of a product and must therefore be handled accordingly.
Obligations under the CRA
Overall, there are two requirements that must be met when making a product available on the market:
- The product must meet essential cybersecurity requirements
- The manufacturer's processes must meet essential cybersecurity requirements
These requirements are specified in Annex I of the Regulation.
Make sure to stay updated as there may be new amendments to the regulation that result in additions and changes to the Annex.
It is crucial to be aware that you are obligated to manage the security of your products throughout their entire lifecycle.
Since the scope of the regulation is very broad, it will also impact products with varying levels of criticality in their usage. Note that there is no differentiation between the requirements for a product; however, the methods you can use to perform a conformity assessment depend on the criticality class of the product in question. Here, there are two focus areas to take into account:
- The essential functionality of the product must fall within one of the categories listed in Annex III or IV of the Regulation.
- The primary function of the product must be crucial for the cybersecurity of other products or be associated with a significant risk of adverse effects.
If the above criteria are met, the product will be classified as important if it is listed in Annex III or critical if listed in Annex IV, which results in the available conformity assessment methods shown in Table 3.
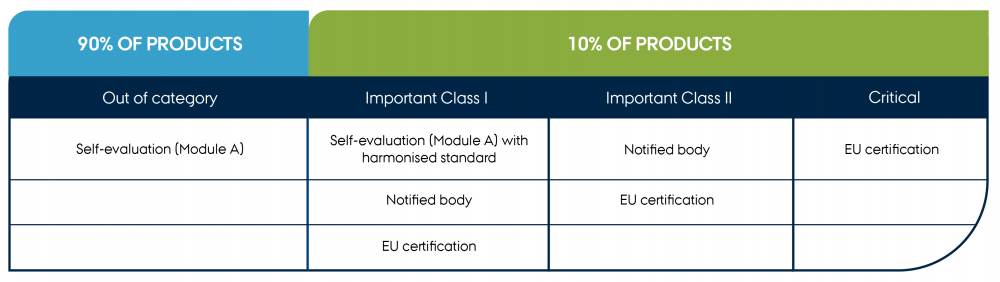
"Conformity assessment methods for product categories" by CyPro under licence CC BY-SA 4.0
Radio Equipment Directive (RED)
The Radio Equipment Directive specifies the essential requirements for products that have the capacity to transmit or receive information wirelessly. The Directive is supplemented by the delegated regulation 2022/30, which specifies the types of products that are subject to the essential requirements related to cyber and information security (Directive's Article 3.3, points d, e, and f).
As a company, you should be aware that this applies to three types of radio products:
- Internet-connected radio equipment.
- Radio equipment that processes personal data, is a toy, is intended for children, or is worn on the body.
- Internet-connected radio equipment that can transfer money.
Obligations under the RED
Depending on which of the above categories a product falls into, it entails up to three essential requirements that the product must meet. The requirement for internet-connected radio equipment reads as follows:
"The radio equipment does not damage the network or its function or misuse network resources in such a way that it causes an unacceptable deterioration of service."
Thus, the requirement mainly focuses on the protection of the networks to which the product is connected. It is important to keep in mind that this applies to all networks – not just wireless ones. The requirement is not necessarily about protecting the product's essential functions.
The second requirement you may be met with concerns data protection and reads as follows:
"The radio equipment is capable of ensuring that personal data of the user and subscriber and their privacy are protected."
Here, the requirement applies only to the protection of data that may be sensitive and the related security features.
Finally, the requirement for the protection of products with the capacity to transfer money reads as follows:
"The radio equipment supports certain facilities that ensure protection against fraud."
This refers to internet-connected radio equipment capable of transmitting money, monetary value, or virtual currency. It is important to note that the general requirements for internet-connected equipment also apply, as the delegated regulation specifies that the mentioned equipment must be internet-connected to be subject to the requirement.
The directive also mandates the use of harmonised standards for conformity assessment of these requirements. This means that a self-assessment (Module A) can only be conducted if an appropriate standard is published in the Official Journal of the EU. Here you will find EN 18031-1, -2, and -3, each of which addresses one of the three essential requirements.
Additional resources and knowledge
NIS2: https://eur-lex.europa.eu/eli/dir/2022/2555/oj
CRA: https://eur-lex.europa.eu/eli/reg/2024/2847/oj
RED: https://eur-lex.europa.eu/eli/dir/2014/53/oj/eng
RED DA: https://eur-lex.europa.eu/eli/reg_del/2022/30/2023-10-27
Expert advice
Cybersecurity legislation is a relatively complex area to navigate, especially if you have no previous experience with CE marking products. The three legislations we have covered all have far-reaching impacts on IoT products and their manufacturers, making them challenging to address. It is advisable to consult external specialists in this field to ensure a good start and to establish a comprehensive compliance plan so that no areas are overlooked or over-/under-implemented. It is also vital to secure management approval, as they will ultimately be responsible for ensuring compliance and may be subject to personal sanctions.
Output
In this module, we have covered the most important aspects of cybersecurity and product legislations in the EU. We have looked at the significance of CE marking, the New Legislative Framework (NLF) and the difference between directives and regulations. We have also explored specific legislations such as the NIS2 Directive, the Cyber Resilience Act (CRA) and the Radio Equipment Directive (RED).
Next step
When you have an overview of the essential requirements that your company or product is obliged to meet, it is important to plan how to achieve compliance. It can be highly advantageous to look at the standards and frameworks that address the issues you are facing. This will be covered in the module Standards.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0
CyPro
You have completed the entire building block
Get your certificate for this completed building block. Request the certificate and we will send you the personal certificate.



