
September 27, 2023
Before you start
This learning module is part of the building block:
The module – in brief
The result of working with this tool is a plan in the form of a visual roadmap that fits the needs of the company regarding IoT cybersecurity. The roadmap is made through collaborative discussions focusing on the importance and timing of core tasks involved in cybersecurity for IoT.
The collaborative work anchors IoT cybersecurity in the company through a common language and a visual representation of the resulting planning-decisions that can be easily shared and used in meetings.
The core tasks are represented in the four building blocks for IoT cybersecurity.
Prerequisites for using the tool
This tool builds on knowledge of the four building blocks for IoT cybersecurity as acquired through the tools Situational analysis and Maturity dialogue.
Please also refer to the Reference sheet for the four building blocks, if you need a recap on the building blocks.
Roadmap for IoT cybersecurity
A roadmap provides peace of mind as it shows what to do when, and makes it clear that nothing is forgotten.
Each of the four building blocks represents a set of tasks for furthering IoT cyber security, and of course the tasks of the building blocks interact and depend on each other.
In the perfect world, all building blocks would be developed in parallel, if needed. But this might not be possible in a busy daily worklife in the company. The rationale of the roadmap is that the building blocks need to be prioritized according to time and importance.
By prioritizing time and importance, the company can address the most important aspects of IoT cybersecurity in the present situation, while at the same time ensuring that the other building blocks will be dealt with in their right time.
This video presents the visual roadmap with focus on the axes and a practical example.
"Introduction to visual roadmap" by CyPro available under licensen CC BY-NC-ND
Visual Roadmap
The roadmap is a grid with two axes where the building blocks get visualised by the company.
Roadmap axes: importance and time
The roadmap template has two axes (see template below):
- The Y-axis represents the importance of the building block (low, medium, and high importance)
- The wording of the building block's 'importance' on the Y-axis is intentionally qualitative to make it open for interpretation by the company. However, if this is too open to make sense of the building block’s importance, the following factors could be considered: 1) The tasks related to the building block: are they important for the company's business? and 2) Needed resource investments for developing the building block: can/should the investments be made now or later?
- The X-axis describes the timing of the building block.
- Here the company decides the time scale. Each column in the roadmap can refer to one year (then the roadmap will be a 5-year plan), six months or two years, or something else depending on the actual planning horizon.
Drawing the building blocks
The roadmap template is divided into squares to invite the company to draw its own four building block shapes by filling out squares. This might leave open spaces in the roadmap, but sometimes all squares will be filled out.
Based on the building blocks' importance and timing for the company, the company will decide on the form of each of the four building blocks. This will be done by filling out squares in the template to visualize the importance and extension in time of each building block in the roadmap. See the example of the completed roadmap below.
“Roadmap” by CyPro under license CC BY-SA 4.0
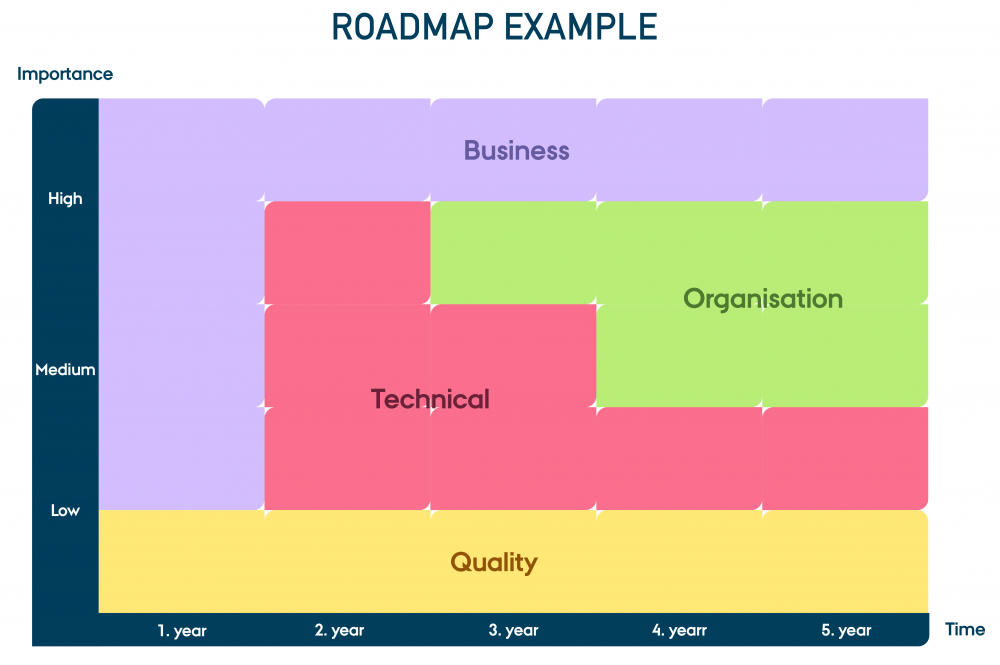
Example of a visual roadmap
“Example for roadmap” by CyPro under license CC BY-SA 4.0
In the example, the building block ’Quality’ has continued attention in the whole roadmap period, like a continuous steady trickle. However, upcomming legislation and/or demands for IoT cybersecurity standards might change this view on the 'Quality' building block, and then some of the 'Business' building block's squares will be colored as 'Quality' instead of 'Business'.
In the first year, the focus is on developing the building block 'Business' and this block remains important as technologies keep on emerging and evolving.
In year 2 and onwards, there is also medium focus on 'Technical' and in years 4 and 5 'Organisation' becomes increasingly important.
Company profile in example
The roadmap profile of this example company represents a company that is developing and anchoring shared practice for IoT cybersecurity. Over time some of this shared practice may evolve into shared structure working with the four building blocks and their interactions and cybersecurity is seen as important for the business model, and IoT cybersecurity is always developed as a part of each new IoT product or service. At the same time, the company has awareness of the need for compliance with regulations, while working steadily to improve IoT cybersecurity practices and organizational integration.
Practical information
This video shows how you can work with the visual roadmap in your company.
"Instruction to visual roadmap" by CyPro available under licensen CC BY-NC-ND
Invite people whose knowledge represents as many aspects of the building blocks as possible, to avoid decisions being postponed to a later meeting. Plan for the meeting with a duration of approx. 2 hours, incl. a short break.
3-4 persons are the best group size for the initial roadmap discussions and planning. More people can be included later to verify, calibrate, and discuss the visual roadmap.
Preparations to the meeting:
- Share the work the company did with the Situational analysis with the participants in due time before the meeting.
- Bring information on relevant plans and strategies that the IoT cybersecurity impacts as the roadmap may interact with these plans and strategies, for example business strategies, quality system, development of new IoT solutions and technologies.
- Print out the empty roadmap template (preferable in A3), one for each participant plus extras. Possible also print out the Reference sheet for the four building blocks.
- Bring coloured pencils or markers for the drawing of the building blocks. Four colours are needed, one for each building block.
Step-by-step guide
This guide is divided into three parts:
- Preparation of the template,
- Drawing the building blocks, and
- Assessment of the resulting visual roadmap.
The whole group works collaboratively in the same roadmap during the meeting and uses their own copy for trials or notes or experimenting with the form of building blocks.
Prepare the shared template
(15 minutes)
This entails deciding on the time horizon for the roadmap, incl. considerations of alignment with other planning horizons in the company such as strategy, customers, development projects etc.
When ready, write the time intervals on the X axis of the shared roadmap.
Draw the building blocks
(20 minutes per building block)
- Consider the content of the four building blocks for the company by consulting the work done in relation to the Situational analysis and Maturity dialogue. If needed, discuss the content in the group.
- Pick a building block and decide:
- How important is this building block for the company's IoT cybersecurity? (Low, medium, high)
- Which period does the building block belong to? How extended in time is it? Are more building blocks needed at the same time because they interact?
- Draw the form of the building block in question by colouring squares in the template to reflect time and importance.
- Reality check of the building block just drawn by discussing:
- Does the company have resources and competences to work with the building block and create the foundation needed for the upcoming/interacting building blocks?
- Is the building block aligned with the remainder of the roadmap? (More important as more and more building blocks are included in the visual roadmap) Make appropriate adjustments if needed. Maybe start over on a new template to clear up mistakes.
- Who is accountable and responsible for driving the building block's development in the company?
- Repeat steps 2 and 3 with different drawing colours until all four building blocks are included in the roadmap.
Assess the resulting visual roadmap
(15 minutes)
Based on the shared visual roadmap, assess the following points:
- Can all participants take responsibility for the plan for the company's IoT cybersecurity as represented by the visual roadmap?
- Does the roadmap sustain the company's need for IoT cybersecurity?
- Does everyone acknowledge accountabilities and responsibilities?
- What is the next step from here?
Outcome
The collaborative work anchors IoT cybersecurity in the company by establishing a common language and a visualization of the resulting planning-decisions that can be easily shared and used in meetings. The holistic nature of the roadmap guides the consideration of the company’s IoT cybersecurity situational context as a whole – making room also for considerations on how the building blocks interact.
The result is a shared plan that potentially spans functions and managerial levels.
It becomes clear which building blocks to focus on as next steps, and the roadmap shows that everything does not have to happen at once.
Expert advice
While making the roadmap it becomes clear that the company 1) should not invest in all building blocks all the time, but rather focus on creating a progessive sequence of building blocks, and 2) should not become over-committeed to one of the four building blocks but keep the development of all four building blocks in mind.
Also the roadmap represents the company's own, individual way of working with IoT cybersecurity.
The technologies in IoT solutions and services keep on evolving which implies that a building block can never truly be finished. Even though a building block is not in focus in the roadmap, the building block still needs ongoing attention and incremental adjustments along the way.
Explicit measurement of the progression with the building blocks might be a sound addition to the existing quality system in the company.
Next step
The next step is to go ahead with the process decided on in the new roadmap. Creating change in perceptions of IoT cybersecurity in the business of the company and allocating resources for the work is done through a learning process closely connected to a company’s real-life context and a collaborative learning process for everyone involved in the company.
The collaborative learning process can be structured and enlightened by the tailored collaborative change tool for IoT cybersecurity.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under Creative Commons.
CyPro
You have completed the entire building block
Get your certificate for this completed building block. Request the certificate and we will send you the personal certificate.



