Prioritizing building blocks for cyber security
2023
This module introduces a tool that helps you agree on the next steps for developing cyber security in the company – and who should be responsible.
maj 30, 2023
This module introduces four building blocks for working with cybersecurity.
The four building blocks provide a 360-degree description of (new) tasks that are part of the company’s cybersecurity effort.
When working with the four building blocks, the company will ultimately have an initial idea catalogue that serves as the foundation for further development of cybersecurity. The company will also establish a common language to facilitate discussions about cybersecurity and gain an understanding of the scope and nature of the tasks required to enhance cybersecurity.
During the process of working with the four building blocks, the following definitions and terminology will recur:
An IoT solution is defined as: Connectivity of production machinery for the purpose of monitoring and control; products and/or services that use sensors, modems or other technology transfer and receive data via the internet, incl. data collected by built-in sensors in machines, as well as data sent to customers’/own systems.
Cybersecurity is a combination of several factors that interact with each other in a company’s operations. To provide an overview, we categorise these factors into four building blocks.
No building block takes precedence over another, as all four building blocks collectively characterise the company’s cybersecurity.
Each building block refers to a task relating to cybersecurity in the company. Or in other words: the building blocks are a way of grouping tools and decisions into four key tasks that the company is facing when developing cybersecurity.
Each company needs to find its own appropriate level of cybersecurity as no s are alike. The definition of ‘appropriate’ depends on the organisation’s business, competences, and resources.
To make it easier for the organisation’s cybersecurity team to discuss the tasks to be carried out, we have made a visual model of the four building blocks for cybersecurity for IoT.
The content of the four building blocks for cybersecurity in the Danish manufacturing industry and related sectors is continuously evolving due to the constant development of new technologies, procedures, and business models.
The building blocks are simplified to help the organisation maintain focus and progress throughout its efforts to develop cybersecurity.
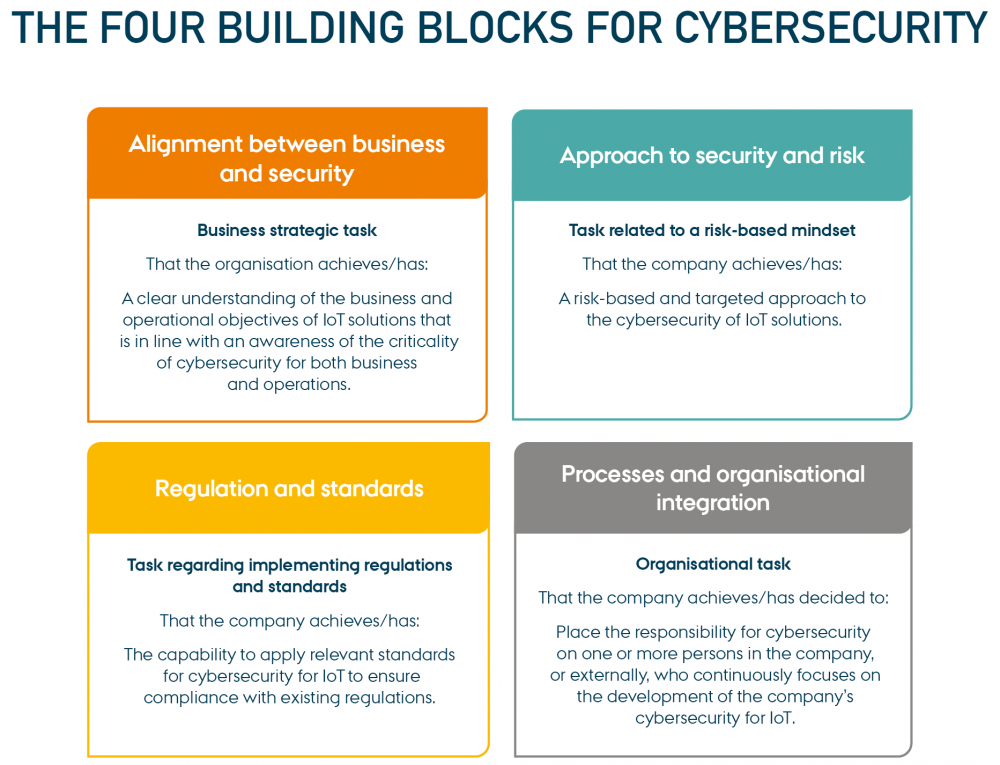
Each of the four building blocks is described in a separate work sheet to help the company gather ideas for the development of cybersecurity in each building block. When all the ideas collected for each building block are combined, they form the company's overall catalogue of ideas for enhancing cybersecurity.
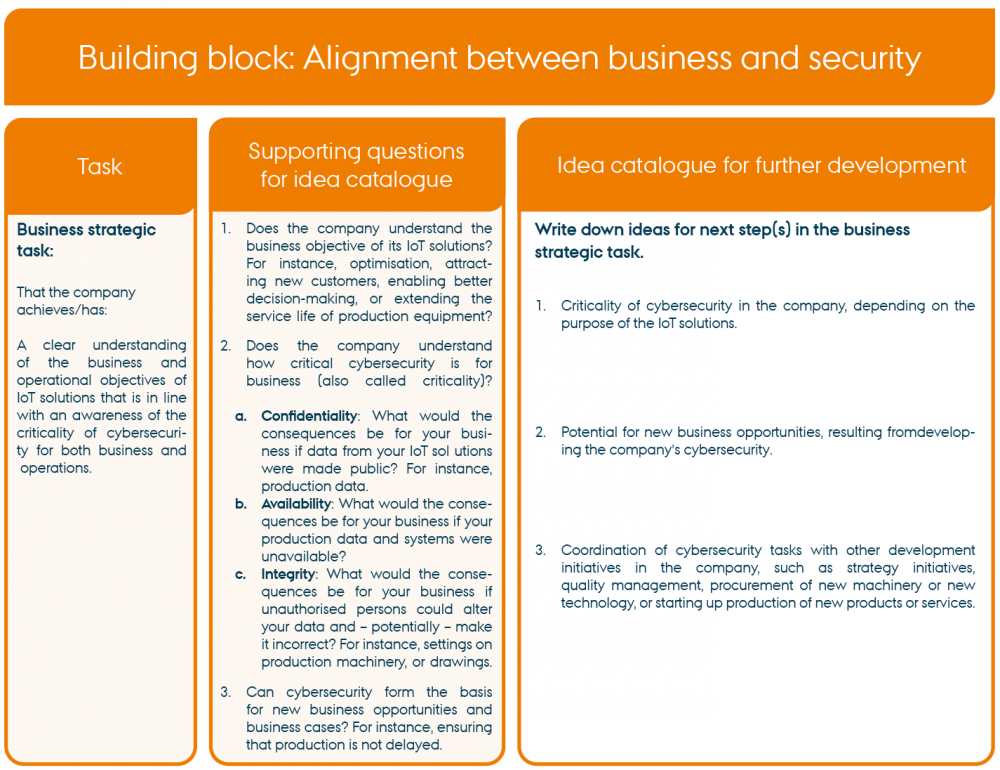
The work sheets can be used as the foundation for discussing the company’s cybersecurity and brainstorm about an idea catalogue for further development of cybersecurity.
Each work sheet is structured as described below (the example shown is the building block Alignment between business and security):
![]()
Building blocks
Printable version of the work sheet for all four building blocks (large format)
1) Begin by scoping the meeting as a preliminary dialogue about the cybersecurity of the company. The purpose is to reflect on cybersecurity, rather than to make extensive and systematic analyses.
2) Decide:
3) All building blocks in turn:
The outcome of this module is a shared idea catalogue that provides a 360-degree view of cybersecurity in relation to business, company, technology, and standards in your company.
In addition, the purpose of the building blocks is to create a common reference for developing cybersecurity across the company, i.e. a common language for discussing tasks and ideas in order to build awareness and launch cybersecurity initiatives.
Some companies are already at an advanced stage in their work with most of the tasks, others are working with 1 or 2 tasks, and yet others have only recently begun to work systematically with cybersecurity. Most importantly: there is no need for companies to work with all tasks at the same time or to the same extent.
So it is quite all right (and expected) if the building blocks evolve over time in each company while the company is working with them.
The building blocks per se do not explain what to do next, or why the company has adopted a certain practice in relation to cybersecurity. To obtain such knowledge, the company should use the tools Situational analysis of cybersecurity, Prioritisation of situational analyses and Goals for building blocks for cybersecurity.
In other words: embedding cybersecurity in the company means that the company actively adapts the building blocks for cybersecurity to its own specific context.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0
