The module - in brief
The purpose of this module is to conduct a situational analysis of the company’s cybersecurity.
The module is based on the four building blocks for cybersecurity, so it is necessary to be familiar with these building blocks in advance. The situational analysis tool provides insights into the company’s current approach to cybersecurity and facilitates the integration of the ongoing cybersecurity initiatives.
The aim of the tool is not to present an alarming view of the company’s cybersecurity; rather, it offers an experience-based view based on the current situation. A systematic overview of the current situation empowers the company to move forward with an open mind.
Integration and adaptation of cybersecurity
The four building blocks for cybersecurity outline the systematic approach required to effectively address cybersecurity in the company.
The building blocks serve as general descriptions that need to be adapted to the unique circumstances of the company, i.e., its current cybersecurity situation, processes, and business requirements.
The situational analysis forms the basis for this adaptation process throughout the company.
The company’s team performs a systematic analysis of practices in relation to cybersecurity within each building block and uses the analysis to assess the situation:
-
- What cybersecurity measures are currently in place in the company that are appropriate and effective?
- How should the company act now to further develop its cybersecurity?
What are the benefits of the tool?
The tool will provide answers to questions like: How does the company solve cybersecurity tasks in a way that is aligned with the need for security, and what needs to be further developed if necessary?
The situational analysis enables the company to make informed decisions when adapting and prioritising cybersecurity tasks.
This is integral to anchoring cybersecurity successfully in the company.
The situational analysis tool
A situational analysis will be carried out for each building block for cybersecurity. The purpose is to make a 360-degree description of how the company solves its cybersecurity tasks at present and evaluate next steps for each task.
The situational analysis is a simple exploration of the three main questions for each building block:
- how does the company work with the building block for cybersecurity?
- why has the company chosen that approach?
- decide how the company wants to go ahead with the building block?
The four completed situational analysis sheets – one for each building block – maintain and structure the cybersecurity situation and serve as the foundation for making decisions on what the appropriate level of cybersecurity should be in the future.
Elements in the tool
Each work sheet contains three main questions in separate columns, including supporting questions for each main question. It is important that the company answers all three main questions for each building block and writes down the answers.
The supporting questions are examples of how the company could solve the cybersecurity task in focus in the situational analysis of the building block. The supporting questions cover considerations, possible decisions as well as specific tasks.
Note that the example shown in the work sheet below is the situational analysis for one building block: Alignment between business and security, and the task is the Business strategic task.
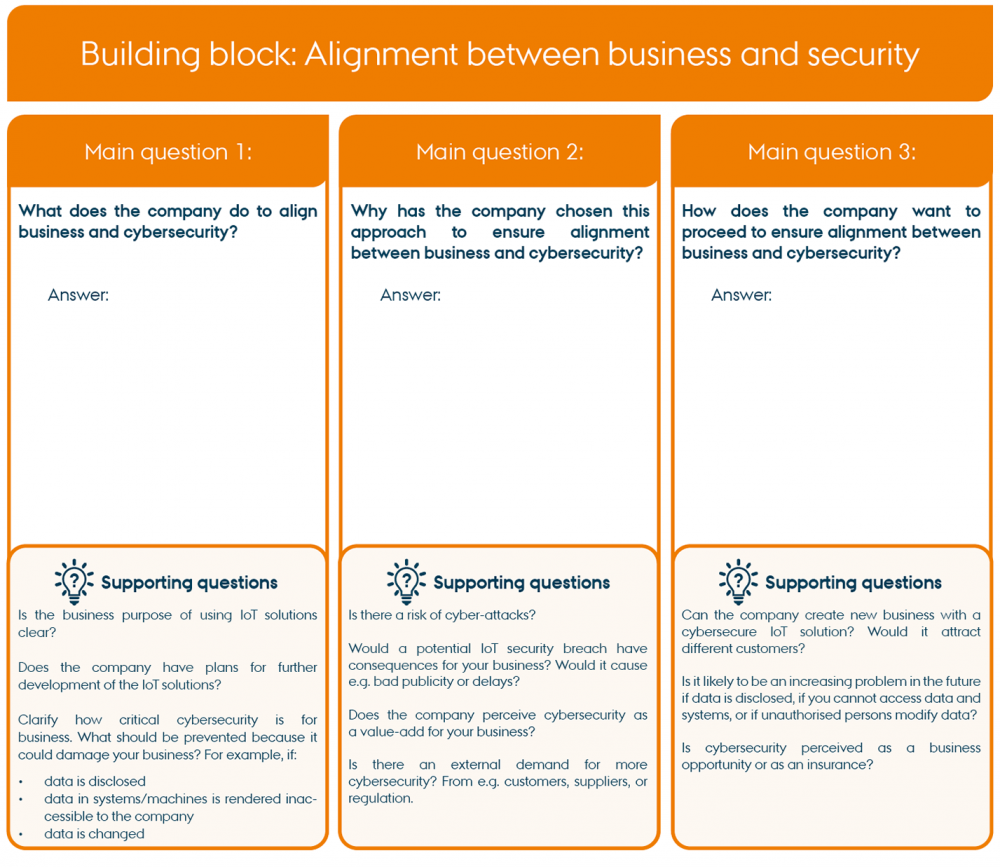
"Example of worksheet for Situational analysis" by CyPro under licence CC BY-SA 4.0

Worksheet for Situational analyses
Printable version of the tool for all four building blocks (large format)
Example of completed situational analysis:
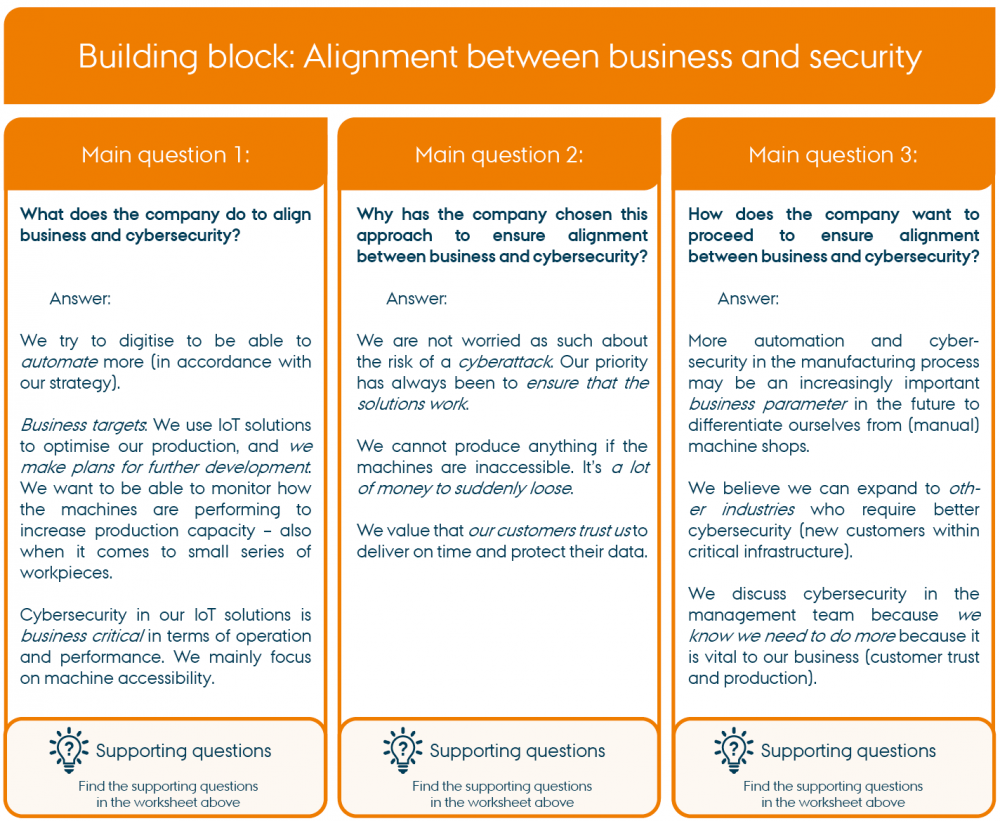
"Example of worksheet for Situational analysis" by CyPro under licence CC BY-SA 4.0
Practical information
In principle, you can carry out the situational analyses in random order, as you need all four analyses to establish a full picture. You can for example follow the steps below:

"Proposal for how to carry out the situational analyses" by CyPro under licence CC BY-SA 4.0
The situational analyses can be carried out at a joint meeting or individually.
The best way to do it is to ask everybody in the company who is involved in or responsible for cybersecurity to carry out the situational analyses together at a meeting with a duration of approx. 1,5 hours.
Situational analyses carried out at a joint work meeting
- Allocate approx. 15 minutes for each situational analysis and 30 minutes in total to get started and for discussions (cf. item 7).
- The most important result of this tool is the dialogue about all four building blocks between those in charge of cybersecurity across functions and departments in the company, and the notes from the discussions that you sum up in the work sheets.
Situational analyses carried out individually
- Distribute the analyses of the building blocks among different professionals, or choose one person who carries out all the analyses.
- Afterwards, the management team or other selected persons organise a meeting to discuss the results of all four analyses. This meeting is called the ‘reality check’ of the analyses in the step-by-step guide (see section 6 below).
Step by step guide
1) If more than three persons take part in carrying out the situational analysis, create smaller groups with two people.
a) Consider composing the groups according to the company’s need to: 1) discuss cybersecurity across technologies and business, or 2) discuss cybersecurity within a specific field, e.g. heads of operations in one group and heads of business in another.
2) Have a look at the main questions in the four situational analyses and agree on which order to complete them in (see example above). Follow this process for all situational analyses.
3) Start the situational analysis by answering main question 1.
a) Discuss the supporting questions. Formulate and write down an answer to the main questions and refer to other documents if needed.
4) Proceed to main question 2.
a) The supporting questions may cause you to consider some of the thought-out reasons behind the existing cybersecurity practice.
b) Discuss why the company has chosen this approach. Formulate an answer and write it down.
5) Finish by answering main question 3.
a) Compare your answers to main question 1 and 2 and consider: what should we focus more on in the future? Consider what practice works well and what to improve.
b) Finally, formulate an answer to main question 3 and write it down.
6) Reality check of the overall picture of the company’s cybersecurity
a) Discuss: Do you agree? Are there items in the situational analyses that should be adjusted?
b) Focus on main question 3 across the four situational analyses: Are the analyses consistent here? Are the proposed next steps realistic all in all?
Outcome
You have now completed an experience-based situational analysis of the company’s cybersecurity based on your specific context.
The insights obtained about the company’s current cybersecurity practices serve as a foundation for developing and anchoring cybersecurity throughout the entire company. Thus, the next steps in the process can therefore be implemented accordingly.
Experience shows that obtaining a systematic overview of the current cybersecurity situation enables the company to proceed with an open mind when it comes to further developing cybersecurity. Therefore, continue to practice active inquiry regarding cybersecurity based on these insights – especially because technological development does not stand still.
Expert advice
It is important to emphasise that a thorough initial analysis of current practice often shows that it is not at all necessary to change everything. That is also a valuable insight. Also, the analysis brings a sense of reassurance that cybersecurity is based on a common understanding of the needs for security in the company’s business. Working with the building blocks also provides the company with a common language for cybersecurity.
Next step
Next step is to prioritise the results of the four situational analyses. That means deciding where to put your efforts based on the systematic understanding of the company’s situation. Use the tool Prioritising building blocks for cybersecurity to begin prioritising.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0





