Prioritizing building blocks for cyber security
2023
This module introduces a tool that helps you agree on the next steps for developing cyber security in the company – and who should be responsible.
maj 30, 2023
The purpose of this tool is to formulate a goal that links a specific action to a specific goal. The goal formulation sets the direction for the ongoing development of cyber security in the company and makes it possible to track progress effectively.
It is a prerequisite for using the tool that the company has collectively prioritised an area (e.g., a building block for cyber security), for which specific goals have to be formulated.
The wording of the tool assumes that the company has worked with building blocks for cyber security.
As part of this tool, the following definitions are used: goal, action, and goal formulation.
Because there is a close connection between goals and actions, the two concepts are defined simultaneously.
One can say that the goal is what the company expects to achieve as a result of an action.
It can be challenging to formulate very specific goals when a company ventures into new areas, and it can be difficult to determine which actions fulfil those goals.
The goal formulation provides clarity between one specific action and one specific goal. The goal formulation is thus the company’s best estimate that a specific action will contribute to achieving a specific goal.
The goal formulation for the upcoming cyber security action is a single sentence that summarises:
The goal formulation can be translated into: IF we take this action to strengthen cyber security, THEN we will achieve this specific goal for our cyber security.
Write down the goal formulation in the following tool that separates the action from the goal but links the two parts together in a single sentence that can be easily shared and communicated across the company.
On the right side of the goal formulation sheet, the company can describe additional specific details on how the action will be carried out to achieve the goal.
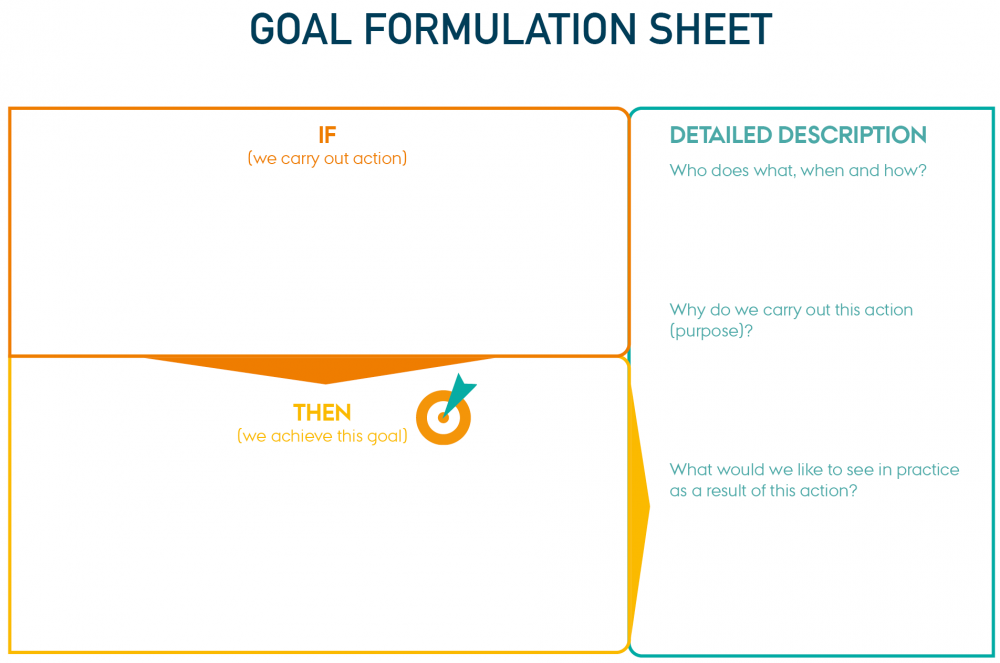
Goal formulation sheet
Printable version of the tool in large format
Below are some examples of goal formulations that can be even further specified with regard to specific tools, communication methods, objectives, and role and responsibility descriptions:
IF we use a systematic tool to model security threats,
THEN we deal with the threats based on their consequences for the company.
IF we communicate tangible cybersecurity goals that are meaningful to the business,
THEN all employees and managers in the company do their best to achieve the goal.
IF we allocate responsibility and resources to an individual for getting familiar with standards,
THEN we obtain a cybersecurity level that suits the company’s operations.
The more concrete the action is, the easier it is to combine a goal with an action.
1) Together, review the building block/cyber security initiative that the company has prioritised for further development: is there any new information that is relevant for the goal formulation? (5 minutes).
2) Each meeting participant individually drafts at least one goal formulation for the action in focus in the goal formulation sheet (10 minutes).
a) Each participant gets their own colour of post-its.
b) Each participant writes: “If we do…” on a post-it and “Then we will achieve goal…“ on another. Then they place both post-it notes in the fields on their own goal formulation sheet, so they form a complete sentence, cf. the examples above.
3) The goal formulations are then presented around the table. Each participant presents and substantiates their overall goal formulation (If… Then) and places their goal formulation sheet on the table (15 minutes depending on the number of participants).
4) After everyone has presented, discuss: Are there similarities? Differences? (15 minutes).
a) Post-its with similar goals and actions are combined: one sheet with similar goals and one sheet with similar actions.
b) If entire goal formulations are identical, combine them on a new shared sheet.
5) Together, decide on one goal formulation for the cyber security action in focus, adjust the formulation, if necessary, write it on a goal formulation sheet, and collectively answer the questions under ‘further details' in the goal formulation sheet (15 minutes).
6) Reality-check the final goal statement: Is the action a realistic and concrete next step, and can the goal be achieved?
The benefit is the establishment of a common language on cyber security and knowledge sharing among key stakeholders in cyber security on how actions and goals are to be connected, e.g. what are ends and means in cybersecurity in the company.
As an additional benefit, it will also be easier to learn from the upcoming action to further cyber security because it can be determined whether this specific action resulted in the expected goal or not.
It can be a surprising experience to hear one’s colleagues express how they understand the relationship between actions and goals. Often, we assume that we are more in agreement about the relations between actions and goals than we actually are.
Having knowledge of colleagues' understanding of the relationship between goals and actions for new cyber security initiatives makes it easier to go through a shared and accommodated change process based on relevant and understandable arguments.
When the next step for cyber security is clearly outlined in a goal statement, the goal statement serves as a steppingstone to combine the other three building blocks for cyber security with the prioritised building block into a realistic plan for the company. This can be done using the tool A roadmap for cyber security.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0
