Risk management - context establishment
2024
december 11, 2024
After having done the threat modelling, you will have identified a list of threats and have some understanding on the consequence should the threat manifest.
Each of these threats can be put into the following table and be evaluated further:
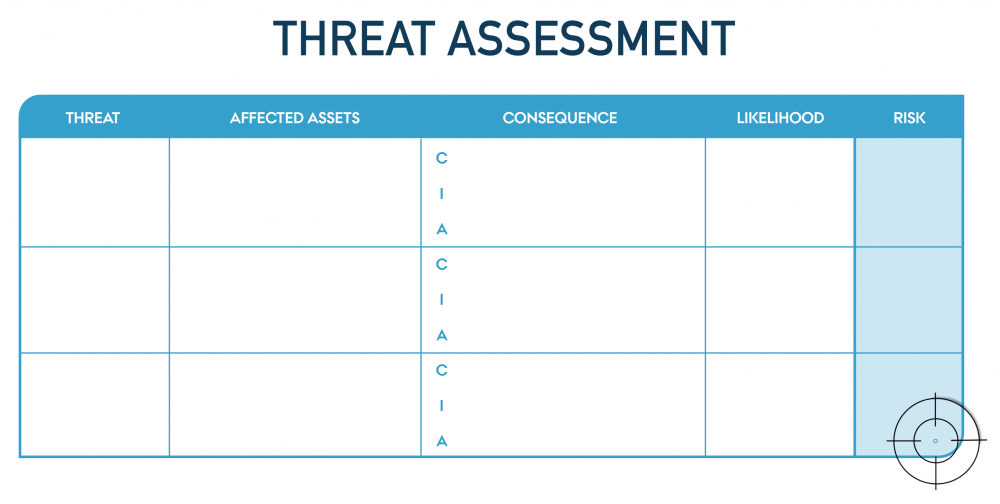
Threat assessment
Print-friendly version of the tool in large format.
The assesments you end up with can be used as input in a risk matrix. Read more about this in the Risk Management module.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0
