
February 16, 2024
Before you start
This learning module is part of the building block:
The module - in brief
The first step in the risk management process is context establishment. The aim of this step is to collect the necessary external and internal information for the risk management process. Moreover, it ensures that the scope of the risk assessment is in line with the context of the organisation.
Context establishment
Context establishment is the first step in the risk management process. The step includes setting the scope and boundaries of the process and defining the risk assessment objectives.
There are several aspects to consider when establishing the context for the risk assessment, e.g., the scope of the assessment, the relevant stakeholders, the methodology, etc. The tools presented summarise the main aspects of it, while the sections below describe each of the aspects in more detail with an example.
The overall process of context establishment is:
-
- Basic requirements
Start by determining the scope of the risk management process. Here you identify what (product or system) you want to assess and what the purpose of the assessment is. Moreover, identify who should be involved in the process, considering both internal and external stakeholders. - Methodology
Next, choose the approach for assessing the risk and define the impact and likelihood of the risk. Based on these two values, you should discuss the overall risk level that is considered acceptable for the organisation. - Threat actors
Finally, determine your key threat actors and discuss what harm they can cause to your organisation/system.
- Basic requirements
Practical information
The context establishment is usually carried out as a workshop. It can be conducted as an independent workshop or as a part of the risk management workshop. It is recommended to involve a diverse range of participants in the process, including management and technical profiles. Set aside one hour to do the context establishment.
It is recommended to carry out the discussion on paper/whiteboard rather than on a computer, so that all participants have the opportunity to be involved.
Basic requirements
Before starting the risk assessment, it is important to define the scope and goal of the work to be carried out. Start by clarifying the purpose of the assessment and what you want to achieve. You may be doing risk assessment for legal reasons, or you may aim at identifying possible vulnerabilities and threats to a product, assessing the operational reliability of a service, or creating a plan to manage and remedy risks. For this purpose, you can use the tools Basic requirements.

"Basic requirements 1-2" by CyPro under licence CC BY-SA 4.0
Basic requirements
Print-friendly version of the tool in large format.
Step-by-step guide
Consider the following key points when scoping the assessment:
- Define the products, systems or services to be covered by the assessment, as well as related components and users.
- Identify the key business objectives of the organisation and determine how the assessment scope relates to them.
- Identify the purpose of the assessment.
- Identify legal requirements and regulatory compliance applicable to the scope. e.g., the General Data Protection Regulation in the EU (GDPR), NIS2, etc.
- Identify the relevant stakeholders on board.
It is important to include the appropriate stakeholders in the process, as their input is essential in mapping assets and their threats, as well as assessing the risk.
Identify which stakeholders should be included in the process and how, whether they be internal stakeholders, e.g., employees, management, or external stakeholders, e.g., customers or investors. We recommend that the group of stakeholders performing the actual risk assessment includes both management and technical profiles. This will ease the following steps later in the process, during which both business and technical assets will be mapped and analysed.
There might not be a need for all stakeholders involved to be part of the entire process. It is advisable to consider this in the beginning and identify which part of the process each stakeholder should contribute to. Furthermore, define the stakeholders’ responsibilities based on their role and knowledge.
Find further inspiration in the IoT door lock example below.
Output
Now, based on the 'Basic Requirements' tool you should have an overview of the system or product you want to assess for risk, why you are doing this, and who you need to involve in the next steps of the process.
Methodology
Another important step in the initial phase of the risk assessment is to define the risk assessment methodology, i.e., define the assessment approach, risk acceptance level, the impact and likelihood of the risk, etc.
There are several approaches to assess the risk, such as asset-based approach that evaluates the assets of the organisation, or threat-based approach that evaluates the conditions that create risk. Each of the approaches has strengths and weaknesses, and choosing the approach will depend on what you need to achieve and the nature of your organisation. Make sure that the chosen approach is aligned with the other approaches for managing risk in the organisation and that the approach is in line with any legal or compliance requirements identified in the ‘Basic Requirement tool’.
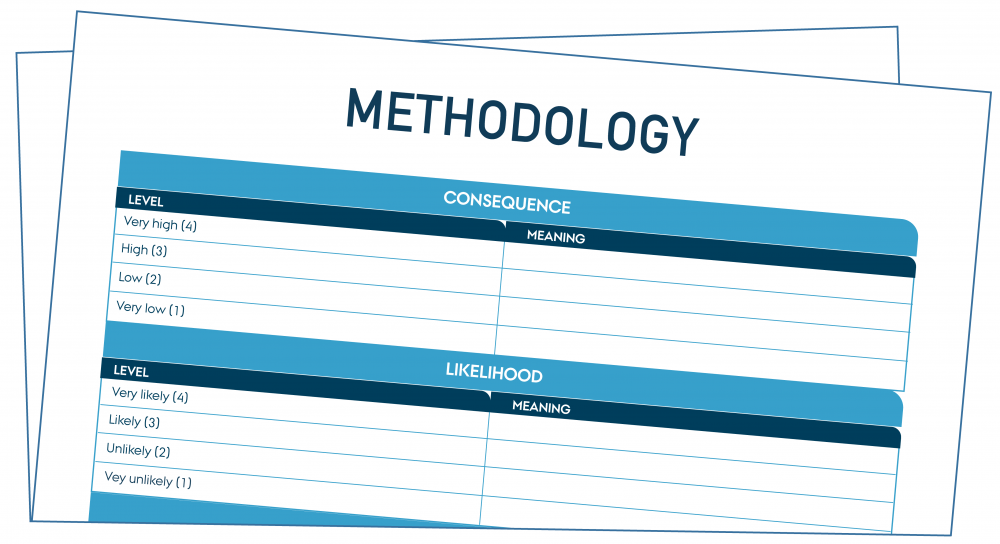
"Methodology" by CyPro under licence CC BY-SA 4.0
Methodology
Print-friendly version of the tool in large format.
Step-by-step guide
-
- Start by defining the meaning of both impact and likelihood, e.g., what does “low likelihood” or “very high impact” mean. For example, “low likelihood” might mean that a threat could occur at some time, but not expected, or “very high impact” might mean an extensive data breach or extremely high financial loss for the organisation. If needed, you can add some notes referring to the chosen approach below your definition and meaning.
- Next, define the risk acceptance level that shows the overall risk level that is considered acceptable for a given period. Risk acceptance level will later be used as a reference point to evaluate the outcome of the risk analysis, i.e., to determine whether a risk is acceptable or not. Moreover, it is used to determine the activities to be carried out during the risk treatment and to check whether the proposed risk treatment is sufficient or if further activities are needed.
- The risk acceptance level is evaluated based on the impact and likelihood of a threat. Impact shows the consequence to the organisation in case the threat happens, while likelihood shows the probability that the threat occurs. It is important to determine the levels of impact and likelihood and discuss what each level means in the context of your organisation and business objectives.
- Finally, you can determine the management activities of the risk owner.
- Start by defining the meaning of both impact and likelihood, e.g., what does “low likelihood” or “very high impact” mean. For example, “low likelihood” might mean that a threat could occur at some time, but not expected, or “very high impact” might mean an extensive data breach or extremely high financial loss for the organisation. If needed, you can add some notes referring to the chosen approach below your definition and meaning.
Note that often there are already some mitigations in place, which might affect the impact and likelihood. Decide how to take existing mitigations into account, e.g., by incorporating them during risk evaluation or risk treatment.
Find further inspiration in the IoT door lock example below.
Output
Now you have an overview of the methodology of the risk assessment, which is a key element in context establishment before continuing the process.
Threat actors
Knowing your threat actors can help in identifying threats (and assess their likelihood) that are targeted towards your organisation in particular.
A threat actor can be an individual, a group or entity that carries out malicious activities with the intent of causing harm to an organisation’s IT security and its data. One of the most common types of threat actors, are cybercriminals. Their aim is to achieve financial gain by stealing or manipulating data and/or sensitive information (such as credit card data, personal information). They can achieve their goal through, for example, phishing attacks, ransomware, or malware. Another example is state-sponsored actors who are backed by governments and conduct cyber espionage, sabotage, or other offensive activities to advance their nation's interests.
See illustration of Threat actors tool below.
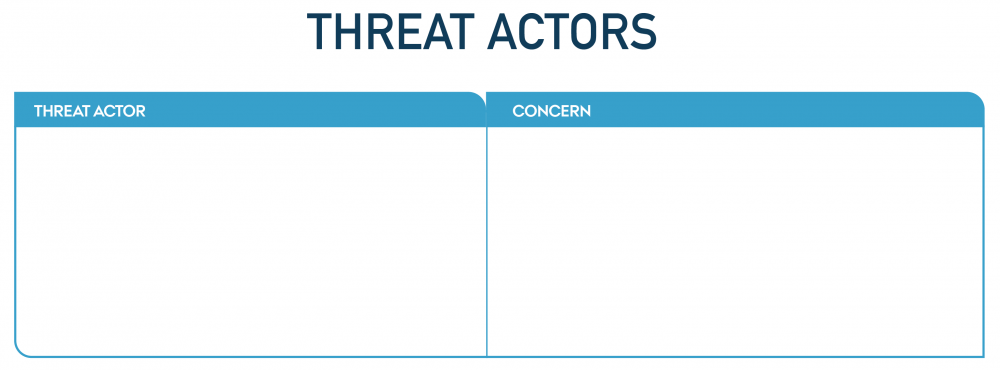
"Threat actors" by CyPro under licence CC BY-SA 4.0
![]()
Threat actors
Print-friendly version of the tool in large format.
Step-by-step guide
- List the key actors you see as posing as a (potential) threat to the given application/system and point out the concerns associated with each of them.
Find further inspiration in the IoT door lock example below.
IoT door lock example
We will use an IoT door lock system as a running example throughout risk management.
Basic requirements
We start by scoping the assessment and filling in the tool “Basic Requirements”.
First, we identify the system and application to be evaluated. For the system, we include the IoT door lock hardware, its wireless communication module, and the Zigbee-enabled hub, along with the cloud infrastructure used for data storage and processing. For the application, we focus on the mobile app, which facilitates remote access and monitoring of the IoT door lock. Additionally, we incorporate integration points such as building management systems and cloud APIs into the scope to provide a comprehensive view of the system’s ecosystem.
In the "Why Do We Do Risk Management?" section in the worksheet, we begin by addressing legal compliance requirements, including GDPR for handling personal data, the Radio Equipment Directive for wireless networks, and anticipated adherence to the coming Cyber Resilience Act. Business continuity and incident response plans are emphasised to ensure the system's resilience and readiness for rapid recovery in the event of incidents. Security requirements are outlined, focusing on encryption protocols, user authentication, and contractual obligations with suppliers and customers. We also document the existing security controls, including measures like access restrictions, and prior risk mitigation efforts.
Finally, under "Other Considerations" in the worksheet, we integrate operational reliability, alignment with business objectives, stakeholder perspectives, and the need for a holistic risk management strategy. This ensures that all aspects of the IoT door lock system are thoroughly addressed, creating a robust foundation for the assessment.
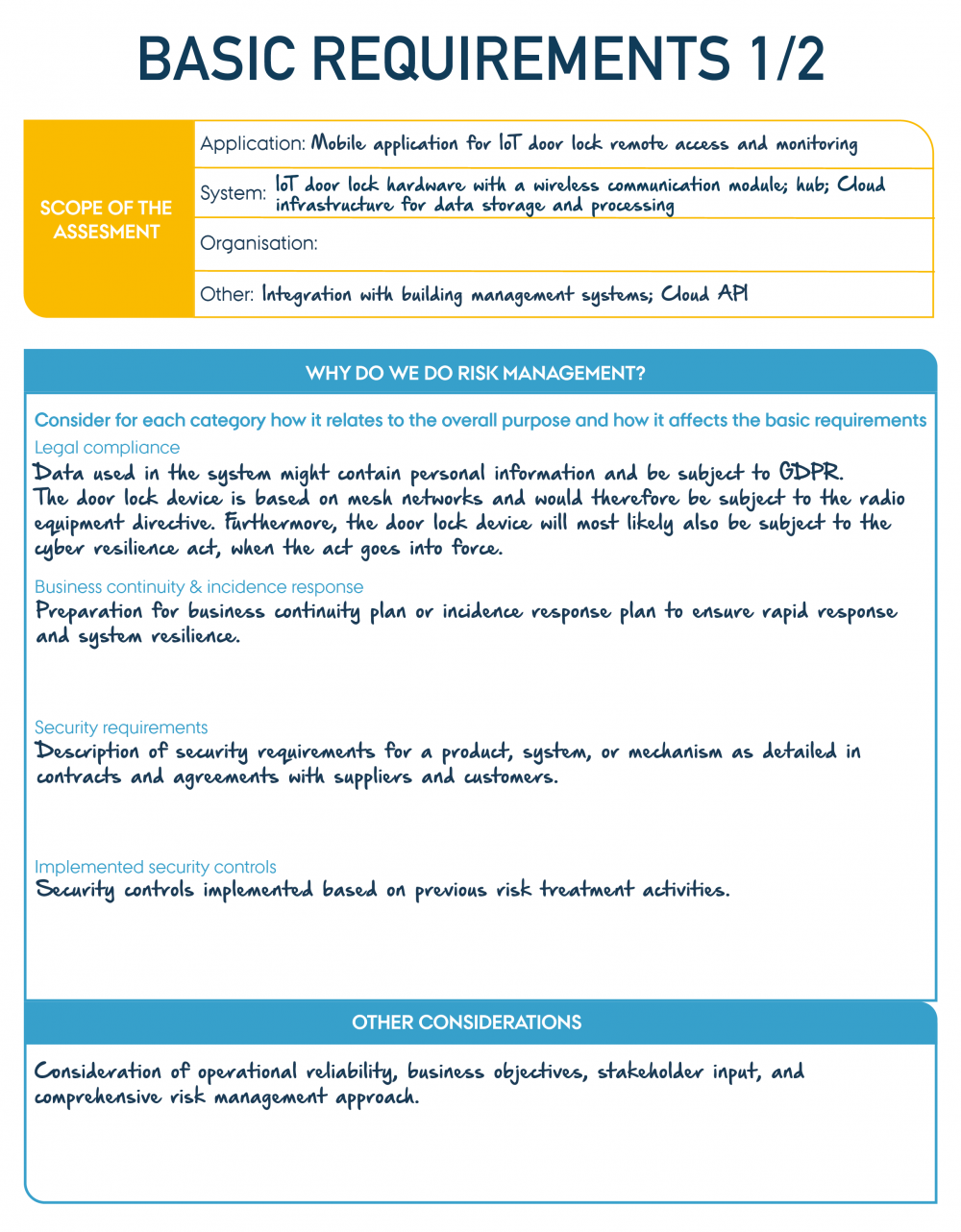
"Example of IoT door lock Basic requirements 1/2" by CyPro under licence CC BY-SA 4.0
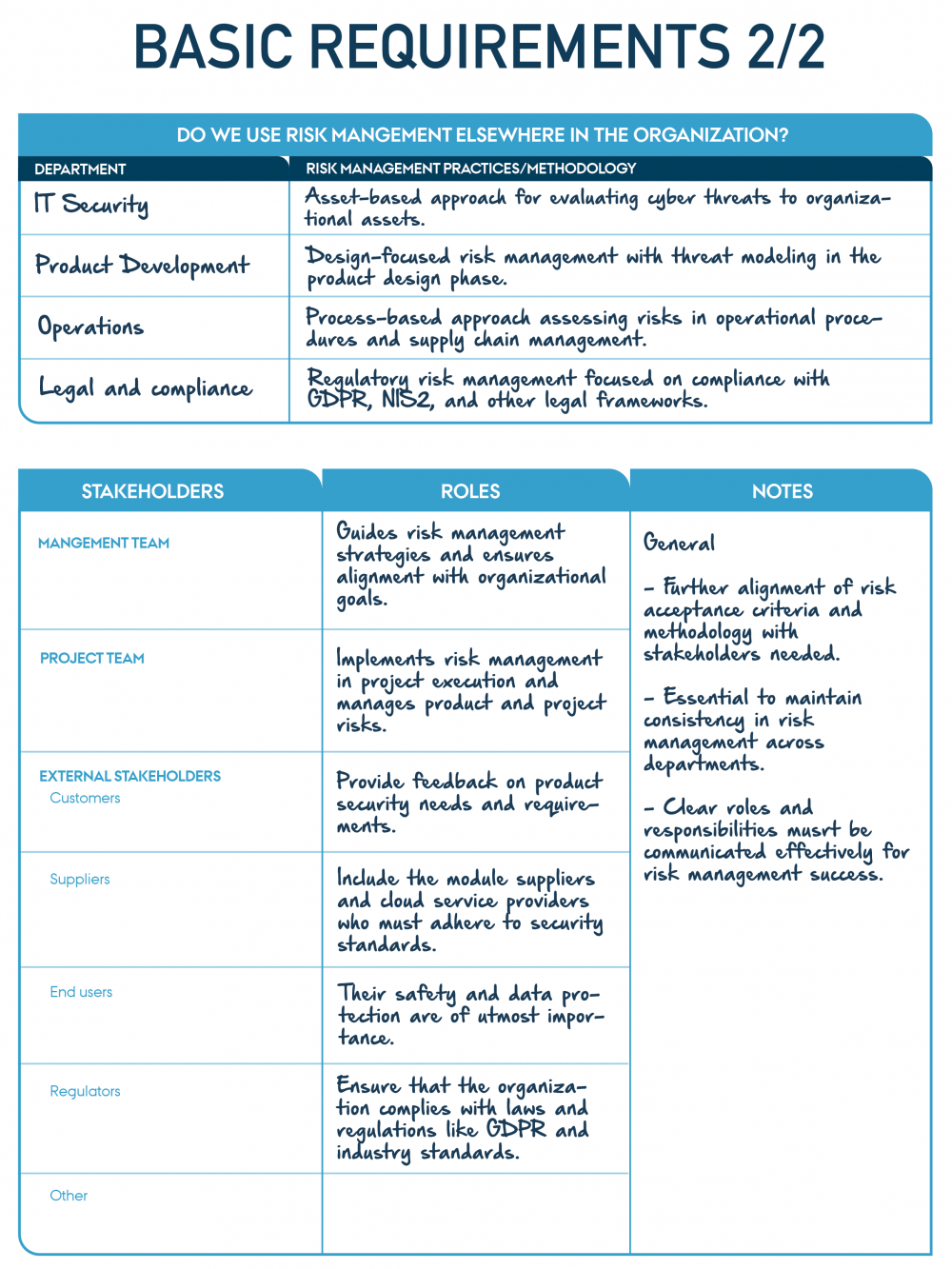
"Example of IoT door lock Basic requirements 2/2" by CyPro under licence CC BY-SA 4.0
Methodology
We establish a clear and structured methodology for assessing risks associated with the IoT door lock system. First, we define impact levels, where “very high” refers to the 5% turnover loss due to unauthorised entry leading to legal/regulatory claims, product recalls, or reputational damage, and “very low” refers to no measurable turnover loss due to minor system glitches that do not impact security.
Then, we determine likelihood levels, ranging from “very likely” where we consider the attacks that have already occurred in the company, to “very unlikely” where we consider the more theoretical attacks that has never been reported in real-world IoT deployments. To ensure accuracy, we consider historical data and vulnerabilities in similar systems.
For risk management, we identify responsibilities based on management levels. The Board oversees risks with a score of 9 or above, while the CEO handles higher risks with scores of up to 8. We assign a risk owner to ensure regulatory compliance, conduct regular assessments, and plan activities for identified risks. These activities include regular reviews of security protocols, implementing measures like encryption, and developing and testing incident response plans. By following this methodology, we ensure a comprehensive and proactive approach to addressing risks and safeguarding the system.
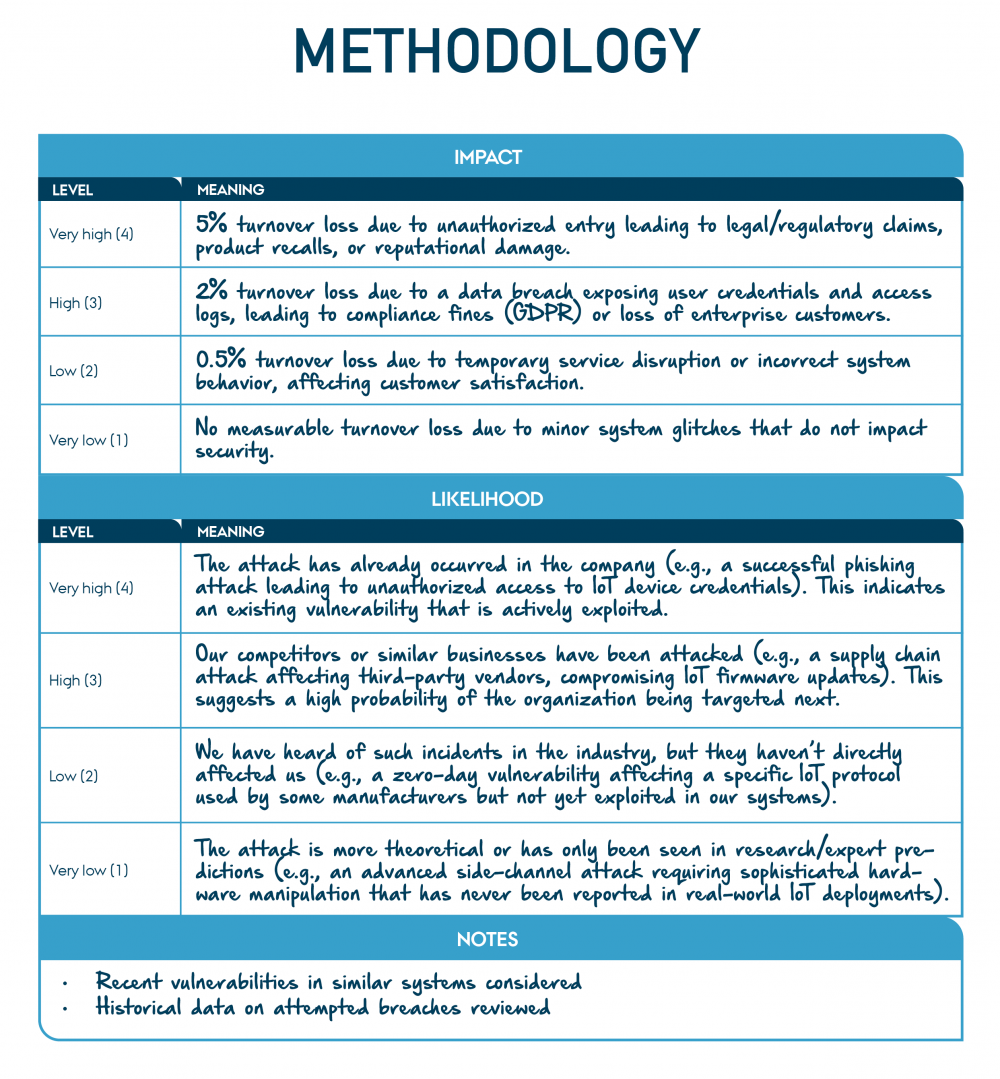
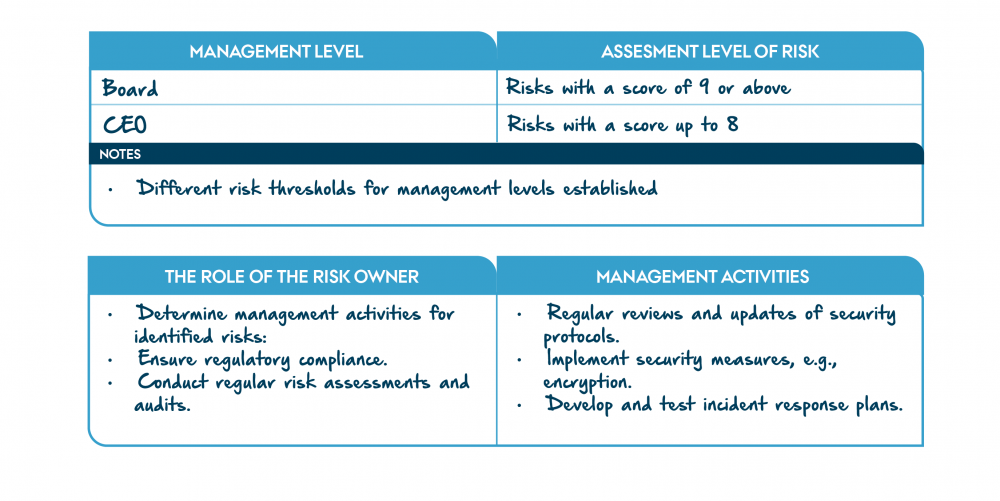
"Example of IoT door lock Methodology" by CyPro under licence CC BY-SA 4.0
Threat actors
We identify potential threat actors and their concerns to better understand the risks associated with the IoT door lock system.
We first consider Nation States, which exploit system vulnerabilities for espionage or to gain strategic advantages, particularly in high-value targets. Next, Cyber Criminals pose a significant threat as they target IoT door locks for unauthorised access, theft, or ransomware attacks, endangering user data and security.
We also include Competitors, who engage in corporate espionage to steal intellectual property or disrupt the services provided by the IoT system. Lastly, we address Activists, who highlight security vulnerabilities as part of their protests against the reliance on IoT devices for security.
By mapping these threat actors and their motivations, we gain valuable insights into potential risks and implement targeted measures to mitigate them effectively.
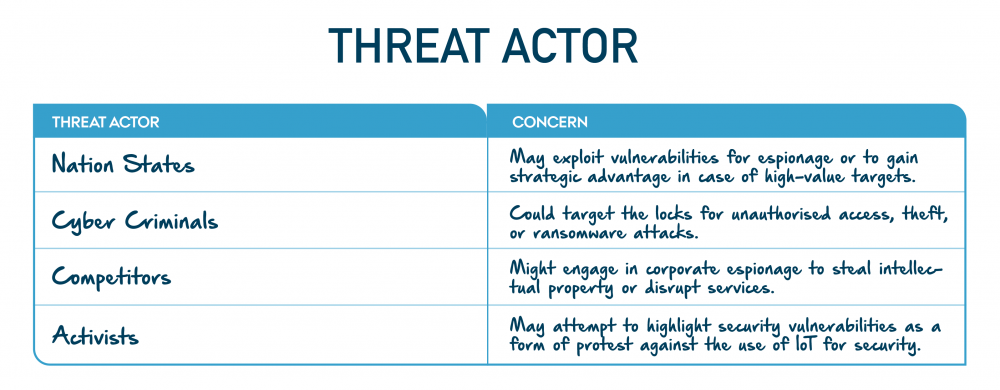
"Example of IoT door lock Threat actors" by CyPro under licence CC BY-SA 4.0
Output
Now you have an understanding and internal alignment of the scope, environment, and objectives of the process, as well as an overview of the potential threat actors, that should be considered when assessing risk.
Expert advice
A risk assessment offers a snapshot view of the risks at the current. As things change, it is advisable to conduct a risk assessment at least once every year or every other year. You should also consider conducting a risk assessment in connection with major changes or before introducing new processes, features, or activities.
Next step
Context establishment is the first step in the risk management process. The next step is to model the system under assessment. It is described in more detail in the system modelling.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence Creative Commons.
CyPro
You have completed the entire building block
Get your certificate for this completed building block. Request the certificate and we will send you the personal certificate.



