
February 16, 2024
Before you start
This learning module is part of the building block:
The module - in brief
After having identified the assets in the system, the next step involves conducting a detailed analysis to establish the potential impact of an incident on assets.
Purpose of asset analysis
If an organisation falls victim to a cyberattack, it can have various consequences depending on the nature of the attack and what is affected. There may also be other incidents that affect the organisation’s assets in diverse ways, although they do not strictly classify as cyberattacks. The purpose of the asset analysis is to conduct a systematic review of the consequences arising from different types of cyber incidents.
"Asset identification and analysis" by CyPro available under licensen CC BY-NC-ND
Practical information
You can analyse the impact in a workshop using the same approach as when identifying assets in the system. As the name suggests, this step involves more analytical tasks compared to earlier stages, which may raise questions that need to be clarified outside or after the workshop – for example by consulting stakeholders who are not participating in the workshop.
Ideally, the analysis should start with a workshop where it is clarified what can be analysed immediately and what needs further investigation after the workshop. Next, each participant can conduct further investigations as needed, after which the group reconvenes to conduct the final analysis.
The participants in the asset analysis should mainly be individuals with business understanding, as they will be best suited to assess the business impact. However, individuals with a technical background can also contribute, particularly with knowledge about how the assets interact: for example, how a compromised asset could facilitate access to assets located elsewhere in the system. Therefore, it is advantageous to involve individuals with business and technical understanding.
Applying the CIA model
Many mistakenly believe that cybersecurity is solely about ensuring that data remains confidential from unauthorised access. Cyberattacks can have other consequences, and in the case of IoT, these can often be worse than data leaks. In the field of IT, the CIA model is used to address such concerns. CIA stands for: Confidentiality, Integrity, and Availability.

"Confidentiality, Integrity and Availability" by CyPro under licence CC BY-SA 4.0
By considering all three elements of the model, you can address the potential impact of a cyberattack. As mentioned during Asset Identification it makes sense in the context of cybersecurity to consider assets as data. If a broader definition of assets has been used, for example one that includes physical objects, you can consider what will happen if the asset is stolen or damaged.
Utilise each of the three elements in the model to assess the criticality if an asset is compromised. Employ the scale defined earlier, as described in Context Establishment. Begin by considering a worst-case scenario and then adjust the assessment to reflect a more realistic scenario. For instance, in a worst-case scenario, a breach of confidentiality in customer data could undermine customer trust, potentially leading to customer loss, which would have a very high impact. Conversely, a minor data leak would probably be of less significance to most customers, resulting in a lower impact.
The scalability of a potential attack should also be considered in the assessment. How many IoT devices will be affected/need to be affected before it becomes a problem? In the case of sensors, individual data points can sometimes be omitted, as there may be naturally occurring errors and deviations that need to be left out in any case.
"CIA-based Asset Assessment" by CyPro under licence CC BY-SA 4.0
CIA-based Asset Assessment
Print-friendly version in large format
CIA-based Asset Assessment
Once you are proficient in making assessments, it is easy to create an overview in a table such as the CIA asset assessment tool. As a start, it can be advantageous to examine each asset separately. The tool Asset Analysis can provide additional support for assessing the assets one by one using the supporting questions for C, I, and A.
"Asset Impact Analysis" by CyPro under licence CC BY-SA 4.0
Step-by-step guide
"Asset identification and analyses - step by step" by CyPro available under licensen CC BY-NC-ND
The assets in the company can be analysed using the CIA model.
- Review the identified assets
Use the list of assets from earlier and analyse each asset one by one. - Identify worst-case scenario
Begin by considering what would be the worst-case scenario if the asset's confidentiality, integrity, and availability were compromised.
You may want to print the CIA-based Asset Assessment Tool for use during the workshop – possibly with support from the Asset Impact Analysis Tool. - Adjust the impact
Take the results from earlier and adjust them to a more realistic situation.
Once you have gone through some of the assets, you can compare the assessments for different assets to ensure a consistent result.
In the following sections, the three elements of the CIA model (Confidentiality, Integrity, and Availability) are further described using the example of an IoT door lock system.
Applying the CIA model on an IoT door lock system
Confidentiality
Most individuals understand the significance of protecting the confidentiality of assets, which is why many security controls prioritise this aspect. Certain assets, such as personal information, subject to GDPR, or trade secrets, clearly require confidentiality protection. However, the importance of confidentiality may not always be apparent for all assets. Yet, when data is combined with other information, it can potentially lead to problems. In the context of IoT, this often involves sensor data, which, when combined with other data, can become personal data. Additionally, certain information may reveal aspects of a company's operations; for instance, data on water or electricity consumption can indicate the company's activity level, which could have an impact on stock prices. Furthermore, it is crucial to protect the confidentiality of assets used for accessing other systems or assets, such as passwords and cryptographic keys.
However, not all data in an IoT system necessitates confidentiality protection. Much of the (unprocessed) sensor data is not particularly interesting, so it may only be necessary to protect the aggregated reports or data. Similarly, commands that control a physical machine often do not require secrecy either, as the result (i.e., the content) of the command can often be inferred from the behaviour of the machine itself.

"IoT door lock example: Asset assessment in terms of Confidentiality" by CyPro under licence CC BY-SA 4.0
Integrity
In the context of IoT systems, protecting the integrity of the data being processed is often important. Even if the data is not deemed critical in terms of confidentiality, unauthorised alterations could lead to unexpected behaviour in the physical component being controlled or inaccuracies in the data used for decision-making, ultimately resulting in wrong decisions.
When data is used to operate a machine, it is crucial to ensure that the machine functions correctly and does not suddenly start during maintenance, for example. Many manufacturers are already aware of this, and there is also regulation in place. Therefore, it is not uncommon to have physical measures in place to prevent personal injury and similar incidents. Often, a compromise of integrity will therefore “only” result in poor system performance or other financial losses.
When collecting data from multiple sensors, it is important to be aware that the data can potentially be manipulated before it enters the system and becomes digital. For instance, an attacker (assuming they have physical access) could blow hot or cold air onto a thermometer and thereby change the measured value without having to alter the data. Generally, it is challenging to fully secure devices when the attacker has physical access, so it might be advantageous to establish mitigating measures on the backend.

"IoT door lock example: Assessment of asset in terms of Integrity" by CyPro under licence CC BY-SA 4.0
Availability
It can be hard to assess the consequences of availability issues. In some systems, data is time-critical, and any disruptions in the continuous flow of data would cause a machine to stop. In those cases, assessing the consequence of an availability issue is relatively easy. However, in most other systems, data is used periodically, and various buffer mechanisms are in place to prevent malfunction if the internet connection is disrupted for a short period of time.
The timing of availability issues can also impact the consequence. For example, if data from a set of sensors is continuously collected but sent in a weekly report, the devices can be unavailable for most of the time, without it causing any problems, as long as they become available when their data is actually needed.
Therefore, it can be difficult to assign an impact score from 1 to 4 directly. It is often necessary to make some notes about the timing and duration of the assumed unavailability of the data.

"IoT door lock example: Asset assessment in terms of Availability" by CyPro under licence CC BY-SA 4.0
The assessment of each asset in the system can be compiled in the CIA-based Asset Assessment Tool, incl. comments, as shown below.
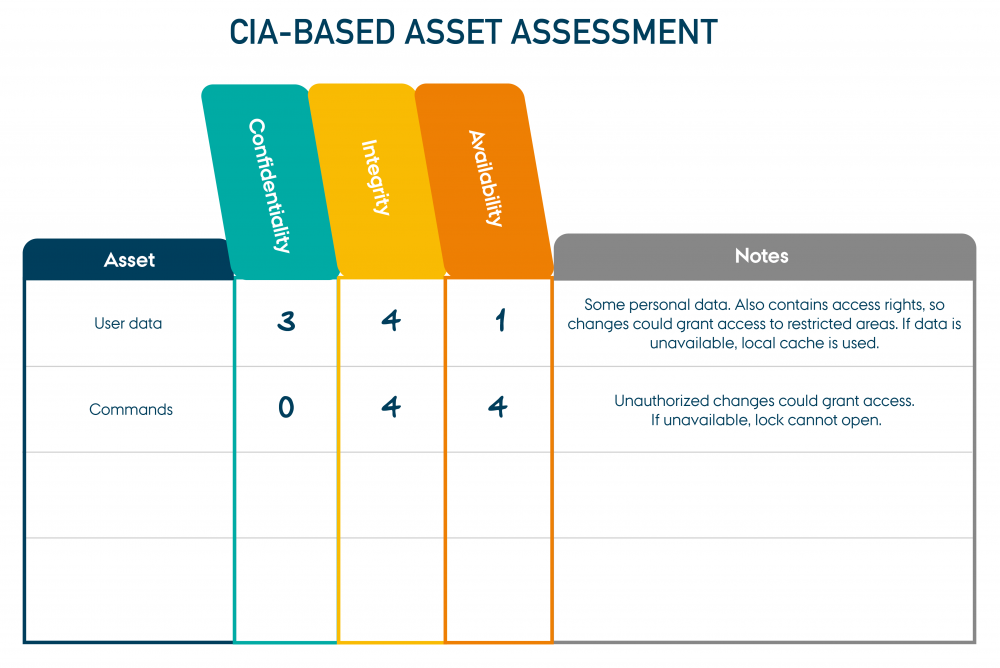
"IoT door lock example: CIA-based Asset Assessment" by CyPro under licence CC BY-SA 4.0
Output
As a result of this analysis, the list of important system assets is enhanced with an assessment of their true importance. This process often prompts several questions, such as: 'What measures are in place to protect xx?' During the threat analysis process, you can leverage this analysis to ascertain what assets are likely to be impacted by a threat and how critical that is.
Expert advice
To ensure consistent assessments, it is important not to have a single person analysing an asset. Involving multiple persons and reaching consensus through voting, discussions, or other means is essential. Whichever method is used, however, depends on the company's culture and levels of trust, as open discussions rely on high trust among participants, while secret voting does not impose the same requirements on the culture.
It is also a good idea to compare assessments and establish their relationships. For example, “We believe that X has an impact of 4, making it worse than Y with an impact of 3. Does that make sense?” You can begin comparing assessments once you have the initial few in place. However, be prepared to revisit and adjust previous assessments if they turn out to be either too optimistic or pessimistic.
Next step
When you have analysed the impact of an incident, the next step is to investigate which incidents and threats you may be exposed to. This is described in more detail in Threat Identification.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under Creative Commons.
CyPro
You have completed the entire building block
Get your certificate for this completed building block. Request the certificate and we will send you the personal certificate.



