Risk management – Asset Impact Analysis
2024
Conducting an impact analysis of assets is an integral part of risk management, serving as a means to minimise the impact of a cyberattack against the organisation.
maj 30, 2023
The purpose of threat modelling is to develop a comprehensive understanding of significant securi-ty aspects in systems, applications, and devices. The process involves adopting the perspective similar to that of malicious hackers while conducting a thorough analysis of the software architec-ture.
Threat modelling can be applied to a wide range of entities, including software, systems, and IoT devices.
During the process, you systematically identify, analyse and assess threats in order to prioritise ef-forts and implement relevant mitigating initiatives.
The increasing use of digital technologies has made companies more vulnerable to malicious at-tacks where hackers attempt to gain unauthorised access to data, disrupt digital processes, or dam-age information. Hence, cybersecurity has become a high priority, and companies work hard to identify known security threats to their systems, applications, and devices to be able to make in-formed decisions about how to address such threats.
Typically, threat modelling is conducted as part of a risk assessment process to identify the vulnera-bilities that may constitute a risk. However, the purpose of risk assessment is to identify and analyse risks from a broader perspective and therefore has a wider scope than threat modelling.
Before initiating a threat modelling process, it is important to understand some key definitions that are used throughout the process.
This illustration shows the steps in the threat modelling process. In the following, we will describe how to conduct each step.

We will use a webshop as a running example to explain the steps in the threat modelling process. The example illustrates the systems involved in ordering, including the interaction between the customer and the logistics provider. For the sake of simplicity, we ignore the surrounding systems and model only on the components that are mandatory for the shopping process.
To perform threat modelling, the first step is to define a scope for the system you want to model: how it interacts with external entities, and what assets you want to protect. Therefore, you must create a data flow diagram of the system that is being modelled, including its trust boundaries, i.e. the components that are (beyond) your control and constitute a potential attack surface. You can use an existing diagram or create a new one.
To establish a common language for the diagram, the following data flow elements can be used, which will also be shown in the web shop example:

![]()
Elements in data flow
Printable version of the tool in large format
An important part of threat modelling is to define the scope of the assessment: This means that you must identify the system/product you want to assess, including related components and users. It is also important to reflect on how the scope aligns with your business objectives. Proper scoping ensures that alle relevant stakeholders are involved in the process. In general, we recommend involving a diverse range of stakeholders, including management and technical profiles.
When assessing an existing system/product, it also pays off to review the existing design documentation and refer to it throughout the assessment.
System modelling and threat mapping are usually conducted as a workshop, often supported by purpose-made tools. In case you do not intend to use any specific tools, you will need a whiteboard/flipboard along with coloured markers, stickers, pens, and printed versions of the worksheets.
Allocate at least three hours for the threat modelling process, which includes system modelling and threat mapping.
We use the web shop example:
1) Brainstorm about the elements in the system.
2) Brainstorm about the data required for the system to work, and where data is located.
3) Map how the elements in the system interact with each other.
4) Mark where there is a trust boundary between elements – for example where different people control different things.

By applying the principles of data flow, you have constructed a data flow diagram for your system.
The diagram gives you an overview of how your system interacts with external entities, as well as the assets you wish to protect. The identified trust boundaries reveal the extent of control you have (or do not have) over these elements, thus highlighting potential attack surfaces.
By constructing a data flow diagram, you have gained a deeper understanding of how your system is designed. You can now proceed to mapping and assessing potential threats to the system. The mapping is shown below and is also based on a webshop example.
If threat modelling is conducted as part of a more extensive risk management process, system modelling serves as a good starting point to identify the assets in your system. Assets refer to the elements or data that are necessary for the system to function or create value in other ways. Assign a unique identifier to each asset, such as a name and/or number, to keep track of them later.
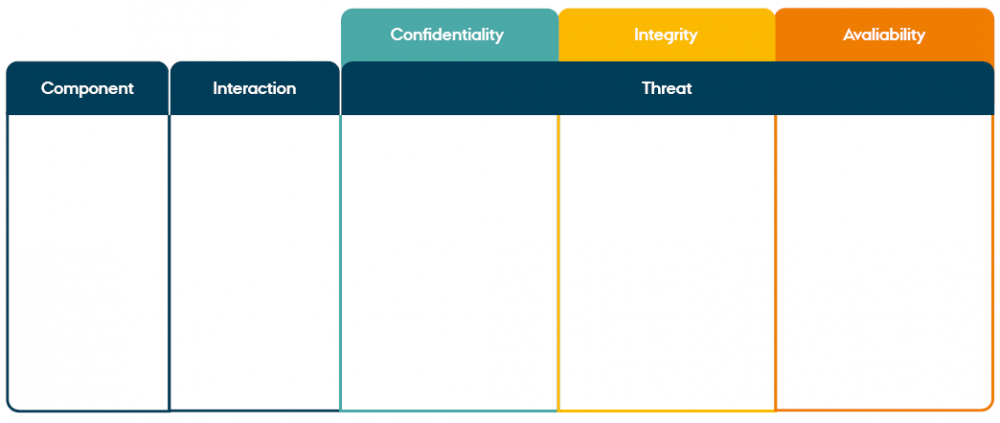
Threat mapping is a tool used to map and understand threats to the system being analysed and how to mitigate those threats. It is a structured process where a system is explored from a security perspective. Furthermore, the process allows for prioritising threats and allocating relevant resources to address them most optimally. Using the flow diagram, we can now examine potential security threats. As a starting point, we trust the internal components, as vulnerabilities are usually found in the boundaries between systems with different trust relationships, so this is where you should look for attack surfaces.
For this process, we use the threat mapping tool shown below:
![]()
Threat modelling
Printable version of the tool in large format
As with system modelling, it is recommended to involve a diverse range of participants in the process, including management and technical profiles. Both the flow diagram of the system and system documentation should be available for reference throughout the analysis.
A threat modelling session is often conducted as a workshop, possibly supported by purpose-made tools. If you do not intend to use special tools, you will need a whiteboard/flipboard, coloured markers, post-its, pens, and printed copies of the worksheets shown in our example.
Allocate at least three hours for the entire threat modelling process.
Tip: Download Alexandra Instituttets Cue cards, to get inspiration for how to map potential threats using the CIA principle (Confidentiality, Integrity, Availability).
Follow this process based on the web shop example to map threat
1) Look into components where data flows across trust boundaries and discuss where potential issues may arise when components/actors with different trust levels exchange data. This will uncover significant and critical threats.
2) Look into components where data flows within a trust boundary and discuss where potential threats may arise. It is not uncommon to have overlooked something or drawn an incorrect trust boundary. There may also be internal threats that should be taken into account.
3) You may also want to look into previously identified assets and consider if it is possible to:
4) Insert the threats you have identified into the threat modelling tool for later reference.
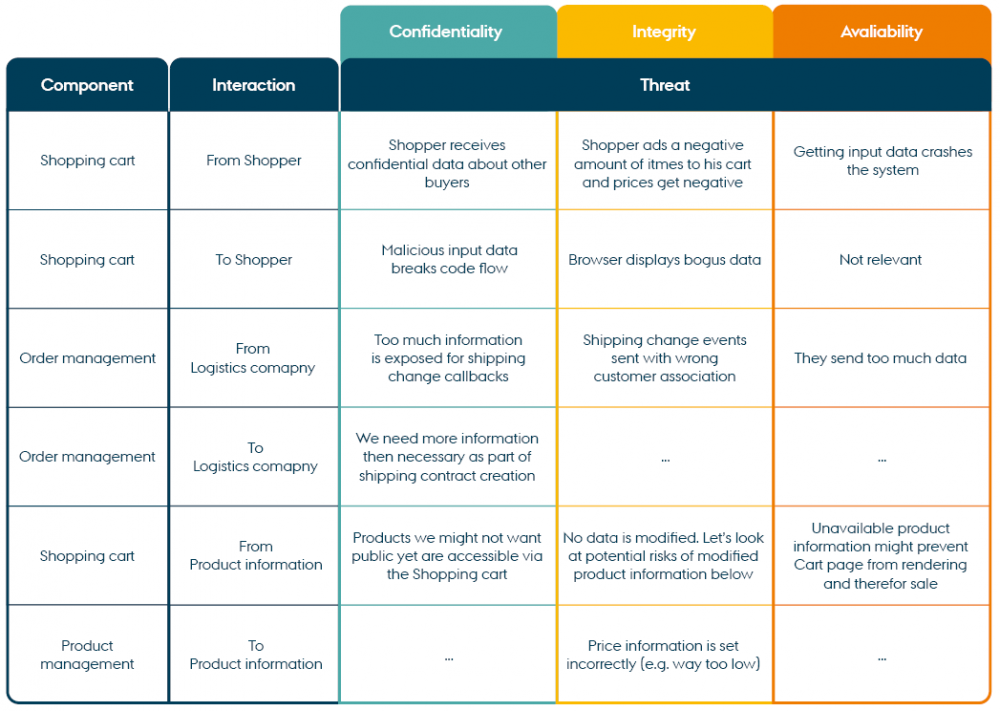
Now we will look into one of the interactions outside the system's trust boundary, namely between the shopper and the shopping cart. Note that there are two interactions to be studied: 1) how the shopper can impact the shopping cart, and 2) how the shopping cart can impact the shopper. First, we will focus on how confidentiality, integrity and availability in the purchasing process (on the server) can be compromised if the shopper performs an unintentional or malicious action.
How can a shopper threaten the confidentiality, integrity, and availability of the shopping cart process?
Confidentiality: Shopping cart content could be sent to the wrong shopper. This can happen simply by modifying a shopping cart id in a cookie or by tampering with an URL.
Integrity: The shopping cart contains a number of items with specific quantities, which later transform into an order. If the integrity is compromised, the quantity of an item could for example be changed into a negative value, which would affect the calculation of the total price, resulting in financial losses.
Availability: The availability of the shopping cart can be compromised if steps in the process take a long time due to unexpected incidents. For example, if a shopper accidentally puts thousands of items into the shopping cart, the recalculation of the total price would affect system performance and impact other customers.
We will now look at the interaction between shopping cart and shopper.
How can the shopping cart threaten the confidentiality, integrity, and availability of the shopper/shopper’s data?
Confidentiality: A data leak from the shopping cart can originate from someone tampering with the code. As in the case above, this could lead to a user receiving data not intended for them.
Integrity: As the shopping cart displays information obtained from other systems, we are displaying data we have no control over. Even though these systems are inside of our trust boundary, it could happen that bogus data is shown to the shopper. Our goal should be to prevent this.
Availability: Not relevant here.
Repeat the above process for all interactions in the data flow diagram. The most important interactions are those crossing a trust boundary, followed by those that occur within a trust boundary. There may also be interactions completely outside a trust boundary, but they are not relevant in trust modelling.
See the example of a completed worksheet below which summarises the threats identified in the webshop example.
We will use an IoT door lock system as a running example throughout risk management.
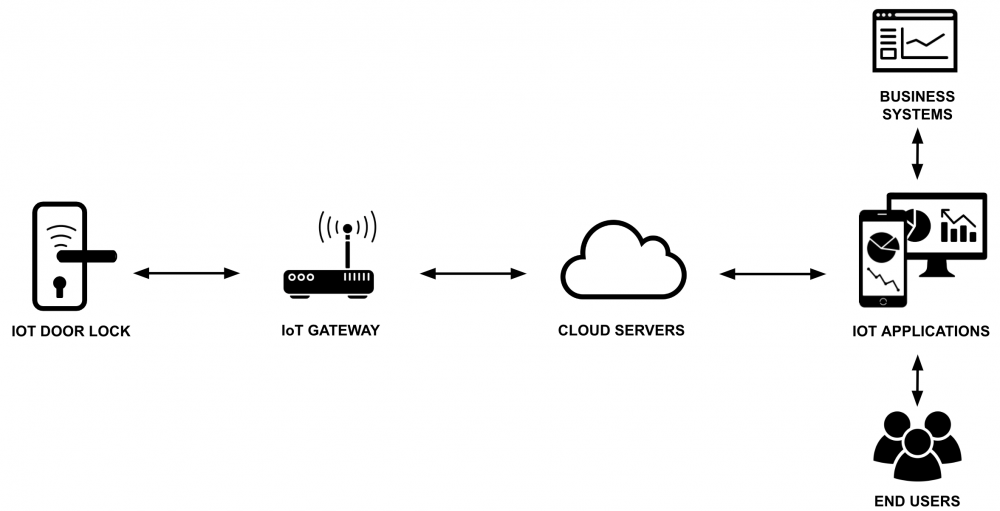
The example consists of an interconnected network of hardware, software, and communications systems, including the IoT door lock hardware with a communication module, a hub, a mobile application for remote access and a cloud infrastructure for data storage and processing.
Below you will find additional download material about threats pertinent to an IoT door lock system.
List of 50 potential threats pertinent to an IoT door lock system
Printable version of the tool in large format
The output of threat modelling is a list of possible threats to the system and corresponding security controls that may reduce their likelihood or impact. Moreover, threat modelling increases security awareness across the company.
Various guidelines and catalogues exist for supporting the threat modelling process. Below are some threat catalogues that provide more details about potential threats.
Threat modelling is a first step in identifying and understanding the risk landscape. Based on the learnings gained from threat modelling, you can go one step further and investigate the various risks to the company. This can be done through a risk assessment process that helps you identify, assess, and prioritise potential risks to your company.
First and foremost, effective risk management enables the company to align its efforts according to the needs. However, it also presents an opportunity to venture into new business cases that may not have been previously recognised. When mitigating the identified risks, it is very important that the process is integrated into the company and has broad support.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0
