Risk management – mapping of assets
2024
Mapping of the organisation’s assets serves as the foundation for managing the risks associated with each individual asset separately.
august 17, 2023
This module introduces you to the risk assessment process, which is an effective tool to identify the security threats and vulnerabilities that your systems, networks, and data are exposed to, as well as the consequences of a potential cyberattack.
The module is intended for a reader without prerequisite knowledge of risk assessment for data security.
A cyberattack is an intentional and malicious attempt to gain access to a company’s or an individual’s systems. The hacker can have various motives such as information theft, financial gain, espionage, or sabotage. The threats to cybersecurity continue to grow and evolve in frequency, vector, and complexity. However, by acquiring knowledge of the potential risks, companies can identify the most significant threats and minimise the likelihood of these events occurring. Although the focus of this module is on risk management in the event of cyberattacks, the methods presented can also be applied to enhance the overall resilience of systems.
Data security risk assessment is a process that involves identifying, analysing, and evaluating the risks associated with an organisation’s information systems and data. The objective of the assessment is to identify potential vulnerabilities and threats, and to develop a plan for managing and mitigating those risks to protect the organisation’s assets and data. This process is called risk management.
This module introduces you to a condensed version of risk assessment and aims to provide an overview of the entire process. A number of tools are presented but the module also refers to other modules and tools.
These steps are part of the risk management process:
Before starting a risk management process, it is important to understand some key definitions that are used throughout the process.
Allocate at least five hours for the identification, prioritisation, and mitigation of risks. It is recom-mended to involve a broad range of key personnel in the analysis. Typically, business understanding is essential for assessing consequences and identifying assets, while technical expertise is essential for assessing the likelihood of an incident occurring.
A risks assessment is usually conducted as a workshop. You will need a whiteboard/flipboard, markers, post-its, and pens.
It is recommended to conduct the assessment on paper/whiteboard rather than using a computer as this allows all attendees to actively participate.
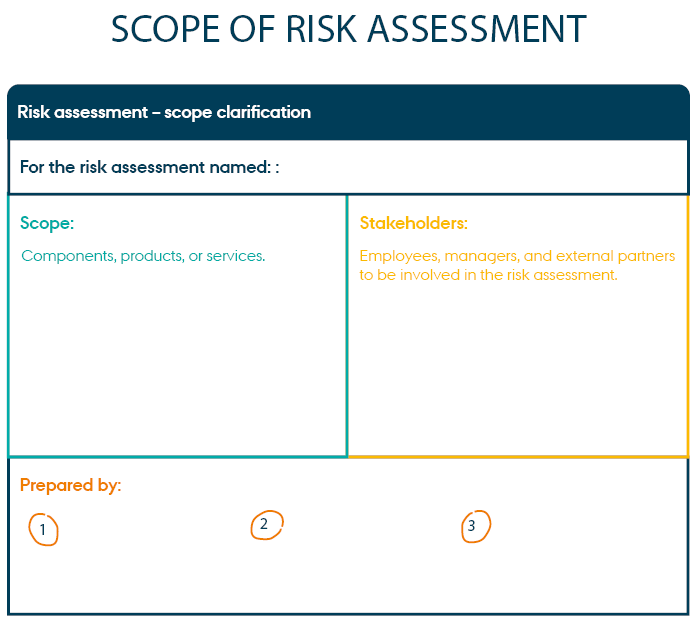
Before you start, you must define the scope of the risk assessment.
1. Scoping
Do not conduct the assessment alone, even if you have limited resources. Seek feedback from others on your scope before inviting everybody to a workshop. If you are new to risk management, it may be a good idea to start with a narrow scope where you focus on a small and well-defined system until you have gained more experience.
2. Mapping of assets
Once the scope of the analysis has been defined, the next step is to map and structure the assets that are to be covered by the assessment. In general terms, assets are components that create value in the system and are important for the system to function. The mapping can be done in different ways but usually involves some kind of brainstorming workshop. The threat modelling module describes how to conduct a workshop.
3. Identify vulnerabilities and threats
Once you have identified what creates value in the system (the assets), the next step is to focus on the threats and vulnerabilities that pose a risk to those assets. Threats can be identified in many ways – from brainstorming to treat catalogues. Threat catalogues are a simple way to get started, although it can be challenging to find a suitable threat catalogue that matches your working context. Often the threats described are either too generic, too detailed, or not sufficiently in line with your scope.
As there is no one perfect solution for everyone involved in conducting risk assessments, it is of-ten necessary to adapt the threat catalogue.
As an alternative, you can conduct a structured brainstorming workshop. Similar to the asset mapping process, the Threat modelling module provides guidelines on how to identify vulnerabilities and threats by conducting a workshop.
4. Prioritise risks
The preceding activity often results in a quite lengthy list of potential threats that need to be ad-dressed. Due to limited resources and budget, it is hardly feasible to mitigate all vulnerabilities. Therefore, it is often necessary to prioritise by focusing on a few selected threats first.
In general, there are two ways to prioritise threats: 1) prioritisation based on the risk matrix or 2) prioritisation based on rating. In both cases, we need to assess the risk for each threat, where we consider the harm that an attack on the system can cause (consequence) combined with the likelihood of the incident actually occurring (probability).
4.1 Prioritisation based on the risk matrix
When prioritising threats using a risk matrix, it is a structured and qualitative approach that ensures more objective results. However, it can be a rather time-consuming process better suited for organisations with a higher level of maturity.
The goal of this method is to prioritise threats based on explicit risk factors such as likelihood and consequence. At this stage, the criticality and relevance of the threats are determined.
Follow these steps to prioritise the identified threats:
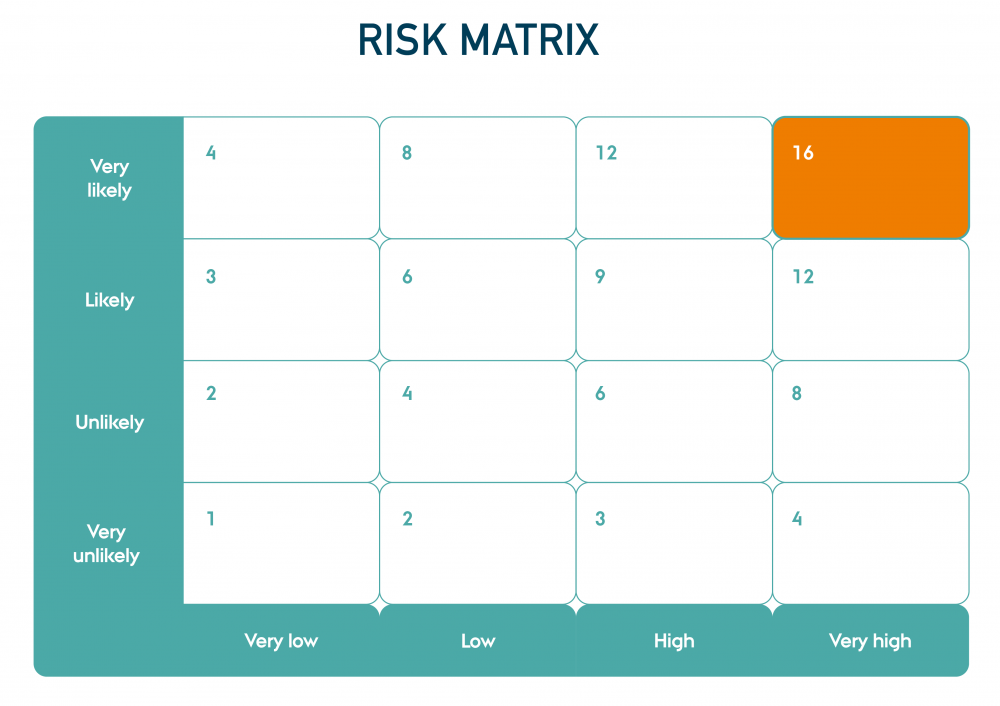
The risk matrix shows the values for different combinations of consequence and likelihood, helping you prioritise which threats to address first. The higher the number, the higher the risk, and therefore it should be prioritized first. You do not necessarily have to calculate the overall risk score as ‘neatly’ as shown in the example. A consequence rated as ‘Very high’, and a likelihood rated as ‘Very unlikely’ can have a devastating impact on a company. So be aware of existential threats and do not rely on the numbers only.
4.2 Prioritisation by voting
Since it can be quite resource-intensive to prepare a proper risk matrix, the threats can be roughly sorted using a voting method. This is an intuitive approach to prioritising threats and is generally suitable for organisations with limited background knowledge of threat modelling and risk management.
The goal is to prioritise threats based on a holistic, intuitive assessment of likelihood and consequence. At this stage, the criticality and relevance of the threats are determined.
If the system already has built-in security controls that may help reduce the overall risk, they should be taken into account when assigning votes.
Before voting, each participant in the workshop is assigned a certain number of votes. The number depends on the total number of threats to be prioritised. The voting can be either confidential or open. Both approaches have their advantages and disadvantages.
Participants cannot give votes to the same threat more than once. The overall risk score for a threat is calculated by summing up the votes it has received.
5. Plan mitigation
Once you have prioritised the risks, the next step is to discuss mitigating measures and how to manage the risks. Since risk mitigation can be an ongoing process, it is very important that management sets a clear goal for achieving sufficient security and an acceptable risk level. When implementing mitigating measures, there are generally four strategies. For each risk, discuss and decide which strategy to pursue – and why.
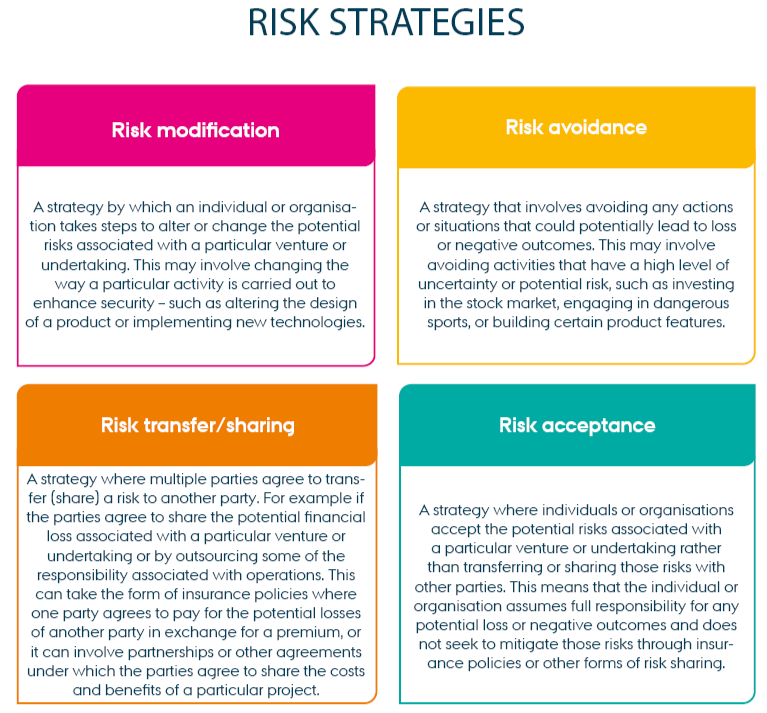
As a starting point, risk modification is a good strategy. Find out which security controls you are already using and whether you can utilise them to reduce the risk to a level that is acceptable to the team and the organisation. Generally, preventive measures reduce the likelihood of an incident, while detective measures can reduce the consequences. Avoiding risk is difficult as not doing anything is not a solution, but you can assess that the risk does not justify the potential gain. Risk sharing can be an option, especially in hosting scenarios, where companies often select a cloud provider to be responsible for operations.
Since many risks cannot be completely eliminated, it is common to end up with some kind of risk acceptance when the potential gain exceeds the risk by a certain margin.
Also, remember to consider any derived risks (from the mitigation) in your risk acceptance criteria.
Residual risk is a term that refers to risks that remain after attempting to mitigate or address other risks. It's a bit like crossing a busy road: You look both ways before crossing and hold your parents' hands. Even with these precautions, there is still a small risk of a car passing by and hitting you. That's what is meant by residual risk.
6. Implement mitigation
Once the critical risks have been identified and suitable risk mitigation actions have been determined for each threat, the next and final step is to ensure implementation. This can be achieved in various ways, depending on the company's specific context and practices. The Development process module describes how the agile process can be managed, while the modules on Building blocks for cybersecurity describes how to anchor those actions across the organisation. In any case, it is essential to assign someone to be responsible for each mitigating measure to ensure successful implementation.
The output of a thorough risk assessment is that it helps you identify specific risks and controls to focus on at any given time. This knowledge is essential for making informed decisions and investments to protect your company.
The assessment is therefore a useful tool that helps you in your efforts to enhance information security, prevent data breaches, and allocate sufficient resources. Last but not least, it enables you to protect your customers’ sensitive data, thus earning customer trust.
Risk assessment is not a one-time exercise but an ongoing process. Your systems constantly change, and so will your information security risks. Conducting regular risk assessments enables you to monitor the changing risk landscape over time and focus your efforts accordingly. Risk asaessments should therefore be conducted on a regular basis (e.g. annually or quarterly) and when major changes occur within the organisation (e.g. new technology implementation, restructuring of key business processes, acquisition, merger, etc.).
Once you have conducted a risk assessment and become familiar with the process, you can expand the scope and conduct it on other products and services. Moreover, you can delve deeper into threat assessment and investigate the threat modelling process.
The processes of identifying both assets and vulnerabilities and threats are described in the module Threat modelling where some of the techniques that can facilitate the process are elaborated.
Once you have identified and prioritised risks, it is equally important to ensure that the necessary mitigative measures are implemented. The module Development process describes how to manage the agile process. The modules Building blocks for cybersecurity describes how to anchor the initiatives across the company. Start with Building block for cybersecurity.

The contents described above have been developed in the project:
’CyPro – Cybersecure manufacturing in Denmark’ by Aarhus University, Alexandra Institut, DAMRC, UGLA Insights and FORCE Technology funded by The Danish Industry Foundation. Material from the project is published under licence CC BY-SA 4.0
